 Vladimir Dzhuvinov gave the innovative and informative presentation “The Key Is Not Enough!” on OpenID Connect Federation at the 2023 OAuth Security Workshop in London. This action thriller of a presentation covers history, goals, mechanisms, status, deployments, and possible futures of the work. The comparisons between X.509 certificates and Federation Trust Infrastructure are particularly enlightening!
Vladimir Dzhuvinov gave the innovative and informative presentation “The Key Is Not Enough!” on OpenID Connect Federation at the 2023 OAuth Security Workshop in London. This action thriller of a presentation covers history, goals, mechanisms, status, deployments, and possible futures of the work. The comparisons between X.509 certificates and Federation Trust Infrastructure are particularly enlightening!
Category: Events Page 2 of 5
 I organized unconference sessions on Wednesday and Thursday at the 2023 OAuth Security Workshop on “What does Presentation Exchange do and what parts of it do we actually need?”. I facilitated primarily by creating an inventory features for discussion in advance, which you’ll find on slide 3. Notes from Wednesday’s session are on slide 4. Thursday we discussed functionality needed and not needed for presenting Verifiable Credentials (with the feature realizations not necessarily tied to Presentation Exchange), which you can find on slide 5. Notes from Thursday’s discussion are on the final two pages.
I organized unconference sessions on Wednesday and Thursday at the 2023 OAuth Security Workshop on “What does Presentation Exchange do and what parts of it do we actually need?”. I facilitated primarily by creating an inventory features for discussion in advance, which you’ll find on slide 3. Notes from Wednesday’s session are on slide 4. Thursday we discussed functionality needed and not needed for presenting Verifiable Credentials (with the feature realizations not necessarily tied to Presentation Exchange), which you can find on slide 5. Notes from Thursday’s discussion are on the final two pages.
Thanks to everyone who participated for a great discussion. I think we all learned things!
The slides used as an interactive notepad during our discussions are available as PowerPoint and PDF.
 I was surprised and deeply honored to receive a Lifetime Achievement Award from Kuppinger Cole at EIC 2023. As I recalled when accepting the award, when Kim Cameron received the same award about a decade ago, he said from the podium “No, don’t do this! My career isn’t over! I’m not done contributing!” Kim always had a wicked wit. ;-)
I was surprised and deeply honored to receive a Lifetime Achievement Award from Kuppinger Cole at EIC 2023. As I recalled when accepting the award, when Kim Cameron received the same award about a decade ago, he said from the podium “No, don’t do this! My career isn’t over! I’m not done contributing!” Kim always had a wicked wit. ;-)
Coincidentally, I described some of the achievements that led to the award during my keynote Touchstones Along My Identity Journey. After a couple of times of me saying “We won an award for that” during the keynote, I was amused that the audience would break out into laughter each subsequent time that I mentioned another award. Like this award, the audience’s reaction was unexpected and delightful.




 I had the distinct honor of being invited to give a keynote talk at EIC 2023. The result was Touchstones Along My Identity Journey. My talk abstract was:
I had the distinct honor of being invited to give a keynote talk at EIC 2023. The result was Touchstones Along My Identity Journey. My talk abstract was:
In 2005, Kim Cameron excitedly told me about digital identity and set my life on a course to “Build the Internet’s missing identity layer”. In this talk I’ll tell key stories from my identity journey — stories of the people, ideas, and lessons learned along the way. I’ll speak of technology and collaboration, usability and business models, solving problems people actually have, and building new ecosystems. Come with me on this journey of exploration, trials, triumphs, and humor as I recount touchstones of the human endeavor that is digital identity.
Kuppinger Cole has posted a video of my keynote on YouTube. I was pleased with how well it went. After the first few sentences, I was in the zone! I hope many of you find the messages in the talk useful.
My slides are also available in (PowerPoint) and PDF.
Special thanks go to the OpenID Foundation for supporting my trip to EIC this year and to designer Alistair Kincaid at MATTR for helping me transcend my usual black-bulleted-text-on-a-white-background presentation style!



 The session Current Work and Future Trends in Selective Disclosure at EIC 2023 covered a lot of foundational work happening in the space of Selective Disclosure right now. Selective Disclosure enables you to have a token with many claims (say, an ISO Mobile Drivers’ License (mDL)), and only release the claims necessary for the interaction — for instance, your birthdate but not your home address. Selective Disclosure enables Minimal Disclosure. This is sometimes realized using Zero Knowledge Proofs (ZKPs) but that’s not always necessary.
The session Current Work and Future Trends in Selective Disclosure at EIC 2023 covered a lot of foundational work happening in the space of Selective Disclosure right now. Selective Disclosure enables you to have a token with many claims (say, an ISO Mobile Drivers’ License (mDL)), and only release the claims necessary for the interaction — for instance, your birthdate but not your home address. Selective Disclosure enables Minimal Disclosure. This is sometimes realized using Zero Knowledge Proofs (ZKPs) but that’s not always necessary.
The agenda for the session was:
-
Mike Jones — Introductory remarks
Daniel Fett — SD-JWT
Kristina Yasuda — ISO mdoc
Tobias Looker — Zero-Knowledge Proofs and BBS
David Waite — JSON Web Proofs and JOSE
All — Closing Remarks and Discussion
Our presentations are available in (PowerPoint) and PDF.
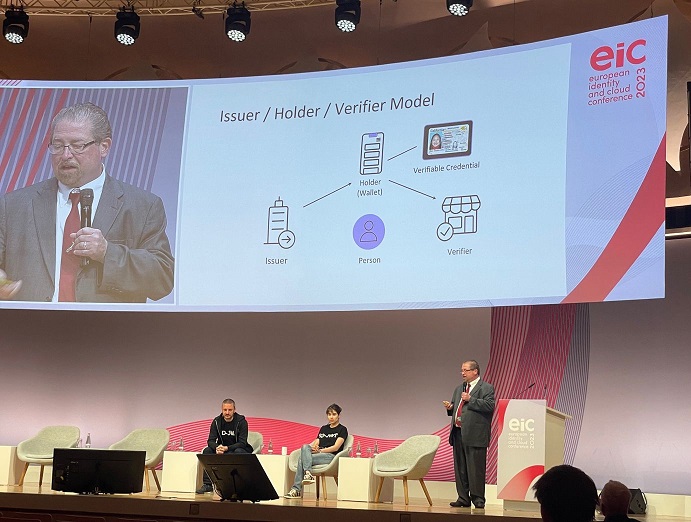
 Giuseppe De Marco and I presented the session How do you know who to trust? at EIC 2023.
Giuseppe De Marco and I presented the session How do you know who to trust? at EIC 2023.
A key question when granting access to resources is ‘Who do you trust?’. It’s often important to know who the party is that you’re interacting with and whether they’ve agreed to the terms and conditions that apply when accessing a resource.
OpenID Connect enables identities of participants to be securely established but doesn’t answer the question of whether a participant is trusted to access a resource such as your personal data. A complementary mechanism is needed to do that. In small-scale and static deployments, it’s possible to keep a list of the trusted participants. However, in large-scale and dynamic deployments, that doesn’t scale.
This presentation described how the OpenID Connect Federation protocol enables scalable trust establishment with dynamic policies. It does so by employing trust hierarchies of authorities, each of which are independently administered. Examples of authorities are federation operators, organizations, departments within organizations, and individual sites.
Two OpenID Connect Federations are deployed in Italy, enabling secure access to digital services operated by Italian public and private services with Italian digital identities. This presentation described why OpenID Connect Federation was selected for them and how it meets their needs. OpenID Connect Federation is also being used by the GAIN PoC.
Our presentation is available in (PowerPoint) and PDF.

 I gave the following presentation at the Monday, April 17, 2023 OpenID Workshop at Microsoft:
I gave the following presentation at the Monday, April 17, 2023 OpenID Workshop at Microsoft:
- OpenID Connect Working Group (PowerPoint) (PDF)
I also gave the following invited “101” session presentation at the Internet Identity Workshop (IIW) on Tuesday, April 18, 2023:
- Introduction to OpenID Connect (PowerPoint) (PDF)
 I’m thrilled that the IETF has restarted the JSON Object Signing and Encryption (JOSE) Working Group. It’s chartered to work on JSON- and CBOR-based representations for Zero-Knowledge Proofs (ZKPs), selective disclosure enabling minimal disclosure, and non-correlatable presentation. The representations are planned to use the three-party model of Issuer, Holder, and Verifier utilized by Verifiable Credentials.
I’m thrilled that the IETF has restarted the JSON Object Signing and Encryption (JOSE) Working Group. It’s chartered to work on JSON- and CBOR-based representations for Zero-Knowledge Proofs (ZKPs), selective disclosure enabling minimal disclosure, and non-correlatable presentation. The representations are planned to use the three-party model of Issuer, Holder, and Verifier utilized by Verifiable Credentials.
See the newly approved JOSE charter at https://datatracker.ietf.org/doc/charter-ietf-jose/03/. The working group will be chaired by Karen O’Donoghue, John Bradley, and John Mattsson, with the assigned area director being Roman Danyliw.
I believe this is a great outcome because the JOSE working group participants already have expertise creating simple, widely-adopted JSON-based cryptographic formats, such as JSON Web Signature (JWS), JSON Web Encryption (JWE), and JSON Web Key (JWK). The new formats will be peers to JWS, JWE, and COSE, reusing elements that make sense, while enabling use of new cryptographic algorithms whose inputs and outputs are not representable in the existing JOSE and COSE formats.
If you’re interested in the work, please join the JOSE mailing list at https://www.ietf.org/mailman/listinfo/jose if you’re not already a member. Also, plan to participate in IETF 116 Yokohama, where we should be able to have the first meeting of the reconstituted working group. I hope to see you there!
As background, the first step in the JOSE rechartering was the JSON Web Proofs (JWP) BoF at IETF 114 in Philadelphia sponsored by Security Area Director Roman Danyliw and chaired by Karen O’Donoghue and John Bradley, during which Jeremie Miller, Kristina Yasuda, Tobias Looker, and I presented. That was follwed by a Virtual Interim JWP BoF in October, 2022, review on the ietf-announce mailing list, and multiple IESG discussions.
All of which brings us back to the (now recurring!) question: “What Would JOSE Do?” Join us and be part of answering it!

 I gave the following presentation at the Monday, November 14, 2022 OpenID Workshop at VISA:
I gave the following presentation at the Monday, November 14, 2022 OpenID Workshop at VISA:
- OpenID Connect Working Group (PowerPoint) (PDF)
I also gave the following invited “101” session presentation at the Internet Identity Workshop (IIW) on Tuesday, November 15, 2022:
- Introduction to OpenID Connect (PowerPoint) (PDF)
 This week at IETF 114 in Philadelphia, we held a Birds-of-a-Feather (BoF) session on JSON Web Proofs (JWPs). JSON Web Proofs are a JSON-based representation of cryptographic inputs and outputs that enable use of Zero-Knowledge Proofs (ZKPs), selective disclosure for minimal disclosure, and non-correlatable presentation. JWPs use the three-party model of Issuer, Holder, and Verifier utilized by Verifiable Credentials.
This week at IETF 114 in Philadelphia, we held a Birds-of-a-Feather (BoF) session on JSON Web Proofs (JWPs). JSON Web Proofs are a JSON-based representation of cryptographic inputs and outputs that enable use of Zero-Knowledge Proofs (ZKPs), selective disclosure for minimal disclosure, and non-correlatable presentation. JWPs use the three-party model of Issuer, Holder, and Verifier utilized by Verifiable Credentials.
The BoF asked to reinstate the IETF JSON Object Signing and Encryption (JOSE) working group. We asked for this because the JOSE working group participants already have expertise creating simple, widely-adopted JSON-based cryptographic formats, such as JSON Web Signature (JWS), JSON Web Encryption (JWE), and JSON Web Key (JWK). The JWP format would be a peer to JWS and JWE, reusing elements that make sense, while enabling use of new cryptographic algorithms whose inputs and outputs are not representable in the existing JOSE formats.
Presentations given at the BoF were:
- Chair Slides – Karen O’Donoghue and John Bradley
- The need: Standards for selective disclosure and zero-knowledge proofs – Mike Jones
- What Would JOSE Do? Why re-form the JOSE working group to meet the need? – Mike Jones
- The selective disclosure industry landscape, including Verifiable Credentials and ISO Mobile Driver Licenses (mDL) – Kristina Yasuda
- A Look Under the Covers: The JSON Web Proofs specifications – Jeremie Miller
- Beyond JWS: BBS as a new algorithm with advanced capabilities utilizing JWP – Tobias Looker
You can view the BoF minutes at https://notes.ietf.org/notes-ietf-114-jwp. A useful discussion ensued after the presentations. Unfortunately, we didn’t have time to finish the BoF in the one-hour slot. The BoF questions unanswered in the time allotted would have been along the lines of “Is the work appropriate for the IETF?”, “Is there interest in the work?”, and “Do we want to adopt the proposed charter?”. Discussion of those topics is now happening on the jose@ietf.org mailing list. Join it at https://www.ietf.org/mailman/listinfo/jose to participate. Roman Danyliw, the Security Area Director who sponsored the BoF, had suggested that we hold a virtual interim BoF to complete the BoF process before IETF 115 in London. Hope to see you there!
The BoF Presenters:

The BoF Participants, including the chairs:

 Here’s the DPoP presentation that Pieter Kasselman and I gave at the 2022 Identiverse conference:
Here’s the DPoP presentation that Pieter Kasselman and I gave at the 2022 Identiverse conference:
- Bad actors are stealing your OAuth tokens, giving them control over your information – OAuth DPoP (Demonstration of Proof of Possession) is what we’re doing about it (PowerPoint) (PDF)
A few photographs that workation photographer Brian Campbell took during the presentation follow.
Mike Presenting:

Who is that masked man???

Pieter Presenting:

 Brian Campbell has published an updated OAuth DPoP draft addressing the Working Group Last Call (WGLC) comments received. All changes were editorial in nature. The most substantive change was further clarifying that either
Brian Campbell has published an updated OAuth DPoP draft addressing the Working Group Last Call (WGLC) comments received. All changes were editorial in nature. The most substantive change was further clarifying that either iat or nonce can be used alone in validating the timeliness of the proof, somewhat deemphasizing jti tracking.
As Brian reminded us during the OAuth Security Workshop today, the name DPoP was inspired by a Deutsche POP poster he saw on the S-Bahn during the March 2019 OAuth Security Workshop in Stuttgart:
He considered it an auspicious sign seeing another Deutsche PoP sign in the Vienna U-Bahn during IETF 113 the same day WGLC was requested!
The specification is available at:
 I gave the following presentations at the Monday, April 25, 2022 OpenID Workshop at Google:
I gave the following presentations at the Monday, April 25, 2022 OpenID Workshop at Google:
- OpenID Connect Working Group (PowerPoint) (PDF)
- OpenID Enhanced Authentication Profile (EAP) Working Group (PowerPoint) (PDF)
I also gave the following invited “101” session presentation at the Internet Identity Workshop (IIW) on Tuesday, April 26, 2022:
- Introduction to OpenID Connect (PowerPoint) (PDF)
 Since Kim’s passing, I’ve been reflecting on his impact on my life and remembering some of the things that made him special. Here’s a few stories I’d like to tell in his honor.
Since Kim’s passing, I’ve been reflecting on his impact on my life and remembering some of the things that made him special. Here’s a few stories I’d like to tell in his honor.
Kim was more important to my career and life than most people know. Conversations with him in early 2005 led me to leave Microsoft Research and join his quest to “Build the Internet’s missing identity layer” – a passion that still motivates me to this day.
Within days of me joining the identity quest, Kim asked me to go with him to the first gathering of the Identity Gang at PC Forum in Scottsdale, Arizona. Many of the people that I met there remain important in my professional and personal life! The first Internet Identity Workshop soon followed.
Kim taught me a lot about building positive working relationships with others. Early on, he told me to always try to find something nice to say to others. Showing his devious sense of humor, he said “Even if you are sure that their efforts are doomed to fail because of fatal assumptions on their part, you can at least say to them ‘You’re working on solving a really important problem!’ :-)” He modelled by example that consensus is much easier to achieve when you make allies rather than enemies. And besides, it’s a lot more fun for everyone that way!
Kim was always generous with his time and hospitality and lots of fun to be around. I remember he and Adele inviting visitors from Deutsche Telekom to their home overlooking the water in Bellevue. He organized a night at the opera for identity friends in Munich. He took my wife Becky and I and Tony Nadalin out to dinner at his favorite restaurant in Paris, La Coupole. He and Adele were the instigators behind many a fun evening. He had a love of life beyond compare!
At one point in my career, I was hoping to switch to a manager more supportive of my passion for standards work, and asked Kim if I could work for him. I’ll always remember his response: “Having you work for me would be great, because I wouldn’t have to manage you. But the problem is that then they’d make me have others work for me too. Managing people would be the death of me!”
This blog exists because Kim encouraged me to blog.
I once asked Kim why there were so many Canadians working in digital identity. He replied: “Every day as a Canadian, you think ‘What is it that makes me uniquely Canadian, as opposed to being American? Whereas Americans never give it a thought. Canadians are always thinking about identity.'”
Kim was a visionary and a person of uncommon common sense. His Information Card paradigm was ahead of its time. For instance, the “selecting cards within a wallet” metaphor that Windows CardSpace introduced is now widespread – appearing in platform and Web account selectors, as well as emerging “self-sovereign identity” wallets, containing digital identities that you control. The demos people are giving now sure look a lot like InfoCard demos from back in the day!
Kim was a big believer in privacy and giving people control over their own data (see the Laws of Identity). He championed the effort for Microsoft to acquire and use the U-Prove selective disclosure technology, and to make it freely available for others to use.
Kim was hands-on. To get practical experience with OpenID Connect, he wrote a complete OpenID Provider in 2018 and even got it certified! You can see the certification entry at https://openid.net/certification/ for the “IEF Experimental Claimer V0.9” that he wrote.
Kim was highly valued by Microsoft’s leaders (and many others!). He briefly retired from Microsoft most of a decade ago, only to have the then-Executive Vice President of the Server and Tools division, Satya Nadella, immediately seek him out and ask him what it would take to convince him to return. Kim made his asks, the company agreed to them, and he was back within about a week. One of his asks resulted in the AAD business-to-customer (B2C) identity service in production use today. He also used to have regular one-on-ones with Bill Gates.
Kim wasn’t my mentor in any official capacity, but he was indeed my mentor in fact. I believe he saw potential in me and chose to take me under his wing and help me develop in oh so many ways. I’ll always be grateful for that, and most of all, for his friendship.
In September 2021 at the European Identity and Cloud (EIC) conference in Munich, Jackson Shaw and I remarked to each other that neither of us had heard from Kim in a while. I reached out to him, and he responded that his health was failing, without elaborating. Kim and I talked for a while on the phone after that. He encouraged me that the work we are doing now is really important, and to press forward quickly.
On October 25, 2021, Vittorio Bertocci organized an informal CardSpace team reunion in Redmond. Kim wished he could come but his health wasn’t up to travelling. Determined to include him in a meaningful way, I called him on my phone during the reunion and Kim spent about a half hour talking to most of the ~20 attendees in turn. They shared stories and laughed! As Vittorio said to me when we learned of his passing, we didn’t know then that we were saying goodbye.
P.S. Here’s a few of my favorite photos from the first event that Kim included me in:
All images are courtesy of Doc Searls. Each photo links to the original.
 I gave the following presentations at the Thursday, December 9, 2021 OpenID Virtual Workshop:
I gave the following presentations at the Thursday, December 9, 2021 OpenID Virtual Workshop:
- OpenID Connect Working Group (PowerPoint) (PDF)
- OpenID Enhanced Authentication Profile (EAP) Working Group (PowerPoint) (PDF)

 I described the relationship between OpenID and FIDO during the October 21, 2021 FIDO Alliance plenary meeting, including how OpenID Connect and FIDO are complementary. In particular, I explained that using WebAuthn/FIDO authenticators to sign into OpenID Providers brings phishing resistance to millions of OpenID Relying Parties without them having to do anything!
I described the relationship between OpenID and FIDO during the October 21, 2021 FIDO Alliance plenary meeting, including how OpenID Connect and FIDO are complementary. In particular, I explained that using WebAuthn/FIDO authenticators to sign into OpenID Providers brings phishing resistance to millions of OpenID Relying Parties without them having to do anything!
The presentation was:
- OpenID and FIDO (PowerPoint) (PDF)
 I gave the following invited “101” session presentation at the 33rd Internet Identity Workshop (IIW) on Tuesday, October 12, 2021:
I gave the following invited “101” session presentation at the 33rd Internet Identity Workshop (IIW) on Tuesday, October 12, 2021:
- Introduction to OpenID Connect (PowerPoint) (PDF)
The session was well attended. There was a good discussion about the use of passwordless authentication with OpenID Connect.
 I gave the following presentation on the OpenID Connect Working Group during the September 13, 2021 OpenID Workshop at the 2021 European Identity and Cloud (EIC) conference. As I noted during the talk, this is an exciting time for OpenID Connect; there’s more happening now than at any time since the original OpenID Connect specs were created!
I gave the following presentation on the OpenID Connect Working Group during the September 13, 2021 OpenID Workshop at the 2021 European Identity and Cloud (EIC) conference. As I noted during the talk, this is an exciting time for OpenID Connect; there’s more happening now than at any time since the original OpenID Connect specs were created!
- OpenID Connect Working Group (PowerPoint) (PDF)
 I gave the following presentation on the OpenID Connect Working Group at the Third Virtual OpenID Workshop on Thursday, April 29, 2021:
I gave the following presentation on the OpenID Connect Working Group at the Third Virtual OpenID Workshop on Thursday, April 29, 2021:
- OpenID Connect Working Group (PowerPoint) (PDF)
 Today marks an important milestone in the life of the OpenID Foundation and the worldwide digital identity community. Following Don Thibeau’s decade of exemplary service to the OpenID Foundation as its Executive Director, today we welcomed Gail Hodges as our new Executive Director.
Today marks an important milestone in the life of the OpenID Foundation and the worldwide digital identity community. Following Don Thibeau’s decade of exemplary service to the OpenID Foundation as its Executive Director, today we welcomed Gail Hodges as our new Executive Director.
Don was instrumental in the creation of OpenID Connect, the Open Identity Exchange, the OpenID Certification program, the Financial-grade API (FAPI), and its ongoing worldwide adoption. He’s created and nurtured numerous liaison relationships with organizations and initiatives advancing digital identity and user empowerment worldwide. And thankfully, Don intends to stay active in digital identity and the OpenID Foundation, including supporting Gail in her new role.
Gail’s Twitter motto is “Reinventing identity as a public good”, which I believe will be indicative of the directions in which she’ll help lead the OpenID Foundation. She has extensive leadership experience in both digital identity and international finance, as described in her LinkedIn profile. The board is thrilled to have her on board and looks forward to what we’ll accomplish together in this next exciting chapter of the OpenID Foundation!
I encourage all of you to come meet Gail at the OpenID Foundation Workshop tomorrow, where she’ll introduce herself to the OpenID community.







