 In October, Microsoft announced that Windows Live IDs would also be OpenIDs. Today the Live ID team published an analysis of what we have learned in operating the Community Technology Preview (CTP) release of our OpenID provider. The post is well worth read and covers, among other things, lessons learned about aliasing and namespaces, having multiple ways to reach the same functionality, and explaining things to users. Enjoy!
In October, Microsoft announced that Windows Live IDs would also be OpenIDs. Today the Live ID team published an analysis of what we have learned in operating the Community Technology Preview (CTP) release of our OpenID provider. The post is well worth read and covers, among other things, lessons learned about aliasing and namespaces, having multiple ways to reach the same functionality, and explaining things to users. Enjoy!
Category: LiveID
Today at the Microsoft Professional Developer Conference (PDC), the Windows LiveID team announced that anyone with a LiveID will soon be able to establish an OpenID for their LiveID. Furthermore, they have established a testing environment where you can try out LiveID’s OpenID support and an e-mail address for you to provide feedback to the team.
One feature of the OpenID 2.0 implementation that I’d like to call your attention to is that they give users a choice, on a per-relying party basis, whether to use a site-specific OpenID URL at the site for privacy reasons, or whether to use a public identifier for yourself — explicitly enabling correlation of your identity interactions on different sites. Here’s what that experience looks like in the preview release:
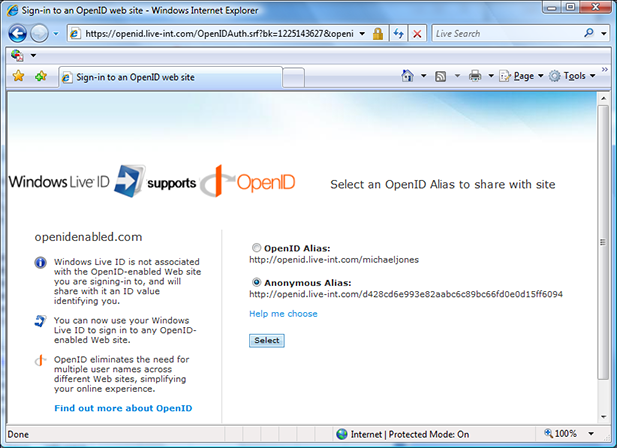
Read more about the preview release here.
 Sean Nolan, chief architect of Microsoft’s HealthVault service, posted an article about giving their users choice for the identities they use to access their information. He announced that in addition to accepting LiveIDs, HealthVault is about to start accepting OpenIDs from two OpenID Providers and is also building native Information Card support. As Sean wrote:
Sean Nolan, chief architect of Microsoft’s HealthVault service, posted an article about giving their users choice for the identities they use to access their information. He announced that in addition to accepting LiveIDs, HealthVault is about to start accepting OpenIDs from two OpenID Providers and is also building native Information Card support. As Sean wrote:
As we’ve always said, HealthVault is about consumer control — empowering individuals with tools that let them choose how to share and safeguard their personal health information. OpenID support is a natural fit for this approach, because it allows users to choose the “locksmith” that they are most comfortable with.
You can certainly expect to see more such options in the future. For example, we are in the process of building in native support for Information Cards, which provide some unique advantages, in particular around foiling phishing attempts.
Talking about OpenID, Sean also wrote:
As we learn more, and as OpenID continues to mature, we fully expect to broaden the set of providers that work with HealthVault. We believe that a critical part of that expansion is the formalization and adoption of PAPE, which gives relying parties a richer set of tools to determine if they are comfortable with the policies of an identity provider.
Please join me in congratulating the HealthVault team on being the first Microsoft service to employ OpenID and for their commitment to providing their users convenient, secure access to their healthcare data.

Last night OSIS and the Burton Group held the third in a series of user-centric identity Interop events where companies and projects building user-centric identity software components came together and tested the interoperation of their software together. Following on the Interops at IIW in May and Catalyst in June, the participants continued their joint work of ensuring that the identity software we’re all building works great together.
This Interop had a broader scope along several dimensions than the previous ones:
- We welcomed new participants a.t.e Software, Fraunhofer, JanRain, LinkSafe, ooTao, Sun Microsystems, Siemens, and ThoughtWorks.
- We tested interoperation of OpenID software (including i-name software) in addition to Information Card software.
- Several kinds of interop between Information Card and OpenID software were demonstrated, including:
- OpenID providers implementing the OpenID phishing-resistant authentication specification using Information Cards to enable phishing-resistant sign-in to OpenIDs, and
- using OpenID Information Cards to supply OpenIDs to OpenID relying parties.
- Unlike previous Interops, the endpoints and testing results are all publicly available so that others can benefit from them.
- Many of the participants have committed to keeping their sites up beyond Catalyst to allow for continued public interop testing. For instance, Microsoft’s sites will remain up at http://www.federatedidentity.net/.
An excerpt from Bob Blakley’s insightful-as-always commentary on the Interop is:
The participants have posted their results on the wiki, and a few words are in order about these results. The first thing you’ll notice is that there are a significant number of “failure” and “issue” results. This is very good news for two reasons.
The first reason it’s good news is that it means enough new test cases were designed for this interop to uncover new problems. What you don’t see in the matrix is that when testing began, there were even more failures — which means that a lot of the new issues identified during the exercise have already been fixed.
The second reason the “failure” and “issue” results are good news is that they’re outnumbered by the successes. When you consider that the things tested in Barcelona were all identified as problems at the previous interop, you’ll get an idea of how much work has been done by the OSIS community in only 4 months to improve interoperability and agree on standards of component behavior.
Be sure to read his full post for more details on what the participants accomplished together. And of course, this isn’t the end of the story. An even wider and deeper Interop event is planned for the RSA Conference in April 2008. Great progress on building the Internet identity layer together!
Kim and I had fun with this video but we’re seriously pleased to be able to show you both using LiveID with Information Cards and DigitalMe in action together. Check it out!
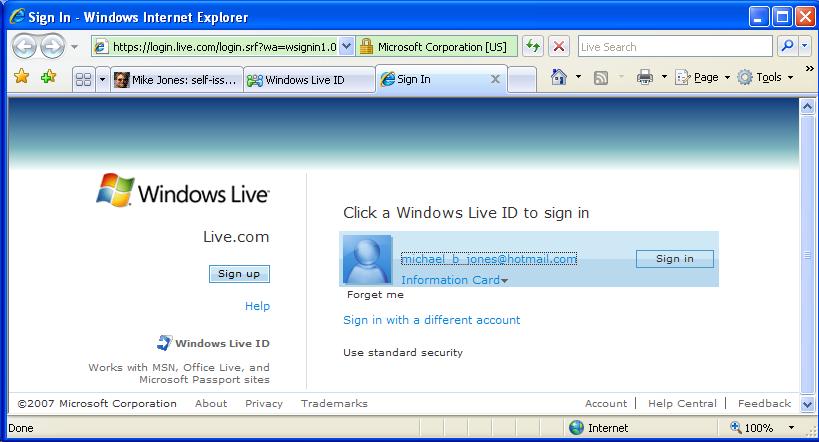
The Windows LiveID team just added beta support for signing into your Windows LiveID accounts with self-issued Information Cards. Now I read my hotmail without ever typing a password. Very cool!
This post announced the support:
Windows Live ID adds Beta support for Information Cards with Windows CardSpace!
Windows CardSpace is a new way to sign in securely and conveniently into websites. And now you can use CardSpace with your Windows Live ID account! Using CardSpace with Windows Live ID means you don’t use a password to sign-in. Instead, just send your Information Card to Live ID to identify you and get signed into Hotmail, Windows Live Spaces or any other site that accepts Windows Live ID. And it is incredibly easy to use CardSpace with your Live ID. Just follow this link (here) to get going in minutes!
If you are using Windows Vista, you are all ready to use CardSpace! If you are on Windows XP or Windows 2003, you will need to get IE 7.0, our newest and coolest browser and .Net 3.0 with CardSpace support (if you don’t already have them). You will also need to add an Information Card to your Live ID account. To install these components and add an Information Card to your Live ID account, visit the Windows Live ID Information Card management page. Also go to that page to make changes to the Information Card added to your Live ID account.
Once you’ve added an Information Card to your Live ID account, sign in using the Information Card. You will be amazed at how easy it is! BTW, that Windows Live ID CardSpace support is still a “Beta”. We are still working on it and know a bunch of things that could be better. But do let us know your wish list; it is always good to get feedback.
Nayna Mutha, Program Manager – LiveID
Rob Franco, Lead Program Manager – Windows CardSpace
Here’s what it looks like:
Congratulations to the LiveID team for helping make the web safer and easier to use!
