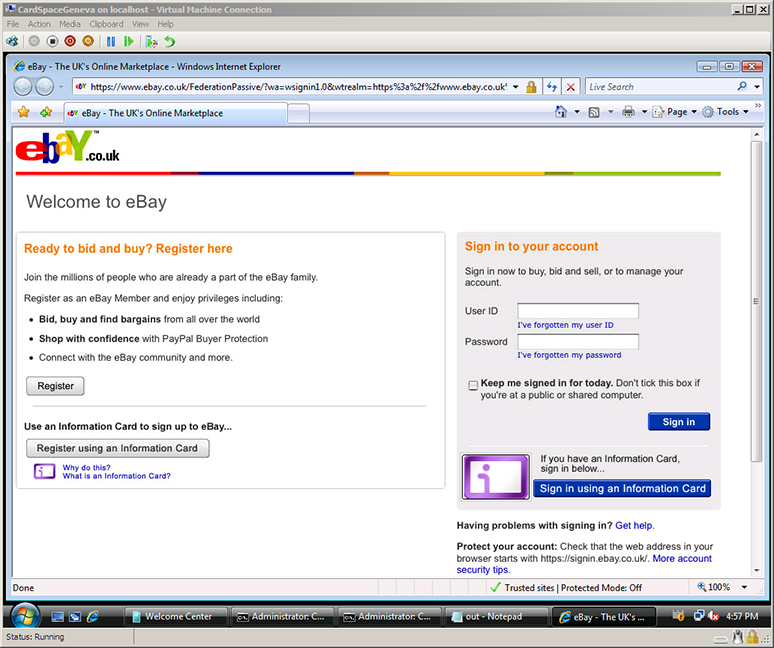
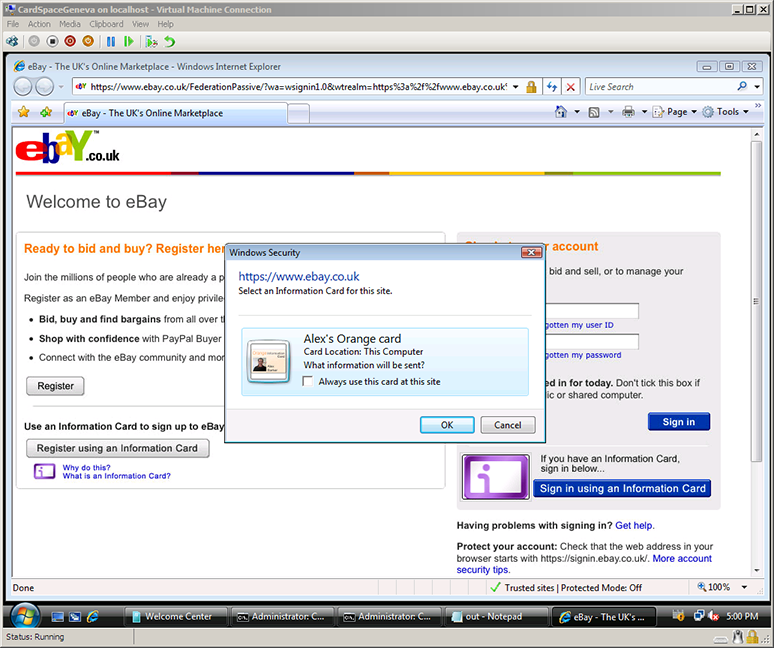
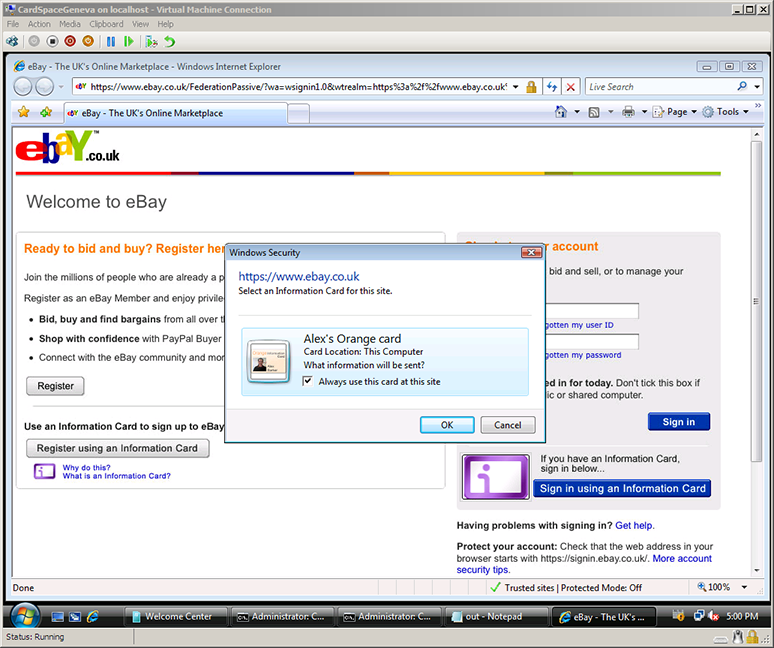
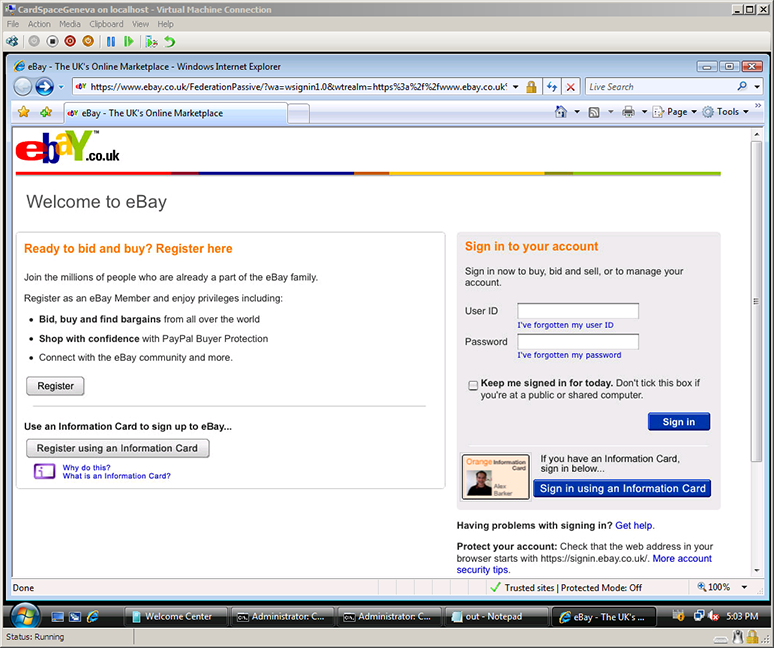
The Internet Safety Technical Task Force has released its report on online child safety: Enhancing Child Safety and Online Technologies: Final Report of the Internet Safety Technical Task Force to the Multi-State Working Group on Social Networking of State Attorneys General of the United States. During its year-long effort, the task force surveyed existing research and evaluated technologies that are relevant to child safety online.
The Internet Safety Technical Task Force has released its report on online child safety: Enhancing Child Safety and Online Technologies: Final Report of the Internet Safety Technical Task Force to the Multi-State Working Group on Social Networking of State Attorneys General of the United States. During its year-long effort, the task force surveyed existing research and evaluated technologies that are relevant to child safety online.
One thing noticeably absent from the report, given the number of different technologies presented to and discussed by the task force, is references to any of them. In the end, the task force took the position that while technologies can help, that none is a silver bullet, and none are a substitute for parents and other adults who are active in children’s lives. I have to agree with them.
The Technical Advisory Board appointed by the task force evaluated possible technological approaches to making children safer online. A number of its members were individuals active in the identity and security communities, including Ben Adida of Harvard, Todd Inskeep of Bank of America, RL “Bob” Morgan of the University of Washington, and Danny Weitzner of MIT. The Technology Advisory Board Report summary included:
In sum, the TAB review of the submitted technologies leaves us in a state of cautious optimism, with many submissions showing promise. The children’s online safety industry is evolving, and many of the technologies we reviewed were point solutions rather than broad attempts to address the children’s safety online as a whole. There is, however, a great deal of innovation in this arena as well as passionate commitment to finding workable, reasonable solutions from companies both large and small. Thus, the TAB emerged from its review process encouraged by the creativity and productivity apparent in this field.
By the end of the review process, the TAB ultimately determined that no single technology reviewed could solve every aspect of online safety for minors, or even one aspect of it one hundred percent of the time. But clearly there is a role for technology in addressing this issue both now and in the future, and most likely, various technologies could be leveraged together to address the challenges in this arena.
Some critics may object to the use of technology as a solution, given the risk of failure and lack of total certainty around performance. However, the TAB believes that although it is indeed true that even the cleverest, most robust technology can be circumvented, this does not necessarily mean that technology should not be deployed at all. It simply means that – even with deployment of the best tools and technologies available to jumpstart the process of enhancing safety for minors online – there is no substitute for a parent, caregiver, or other responsible adult actively guiding and supporting a child in safe Internet usage. Likewise, education is an essential part of the puzzle. Even the best technology or technologies should be only part of a broader solution to keeping minors safer online.
Makes sense to me…
From a personal perspective, I’d like to thank the task force for giving me the opportunity to describe how Information Cards can be used to convey verified claims about individuals, and to thank IDology and Novell for making this real with a working demo of verified age cards for the task force.
I also enjoyed working with Jules Cohen and Chuck Cosson of Microsoft’s Trustworthy Computing and Law and Corporate Affairs groups on the identity technology aspects of Microsoft’s inputs to the task force. I have enormous respect for the balanced and thoughtful perspectives they brought to the discussion, as exemplified by their paper Digital Playgrounds: Creating Safer Online Environments for Children, which was submitted to the task force. Their proposal that existing offline identity proofing ceremonies could be leveraged to enhance safety online resonated with many of the task force members.
I expect media and blog coverage of the report to be active over the next few days. An early sampling includes:
These are important and interesting issues. It’s a discussion well worth following and participating in.
![]()
![]() Microsoft has released an additional rendering of the Information Card Icon with a 3:2 aspect ratio, which can be used in addition to the existing 10:7 aspect ratio renderings. Quoting from the updated Frequently Asked Questions document:
Microsoft has released an additional rendering of the Information Card Icon with a 3:2 aspect ratio, which can be used in addition to the existing 10:7 aspect ratio renderings. Quoting from the updated Frequently Asked Questions document: