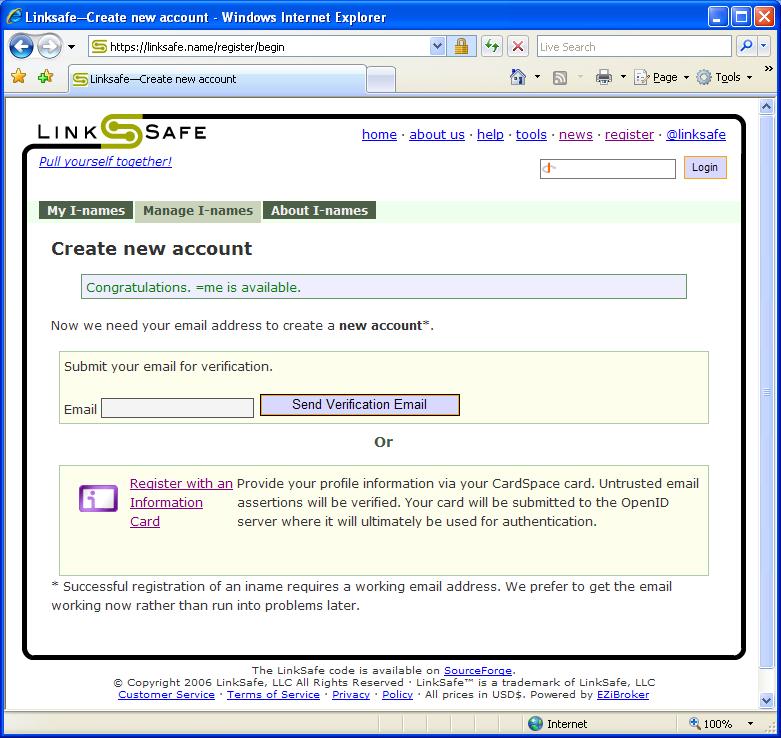
As Vittorio excitedly pointed out, you never have to enter a password to create or use an OpenID at MyOpenID.com. Kim’s excited about this too. So am I. When I wrote:
The JanRain team has done a fantastic job integrating account sign-up, sign-in, and recovery via Information Cards into their OpenID provider. I’m really impressed by how well this fits into the rest of their high-quality offering.
I should have expanded upon my point “fantastic job integrating account sign-up” to explicitly call out that no passwords are needed. Notice the Information Card button on the sign-up page below. Thanks Vittorio and Kim, for sharing your excitement about this. I’m hoping that as other sites integrate Information Card sign-in to their user experience that they’ll also follow this example (and the guidance in the deployment guide) and enable password-less sign-up with Information Cards.
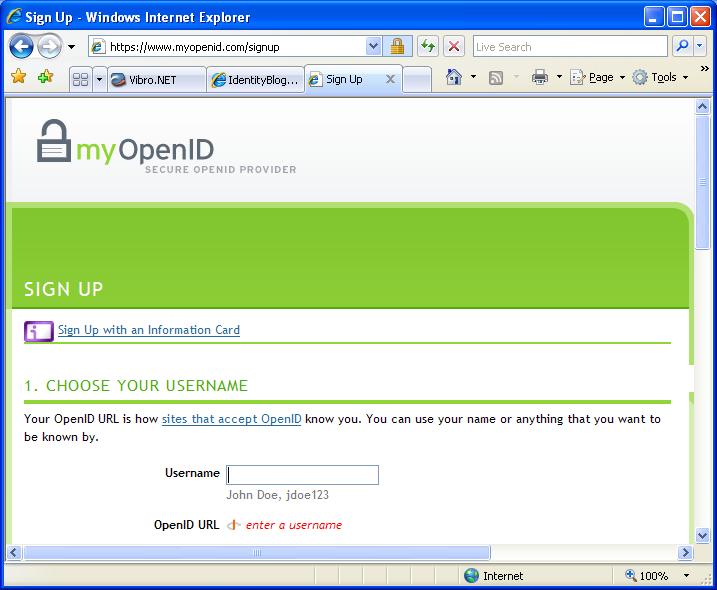
Related to this is JanRain’s earlier announcement that they are including PAPE support in their widely-used OpenID relying party libraries. As Kevin Fox wrote:
Just a note to let everyone know that we are developing and will release relying party libraries supporting PAPE once the specification is finalized.
We have deployed an example relying party available here:
openidenabled.com/python-openid/trunk/examples/consumer/
The example fully supports OpenID 2.0 draft 12, and can request phishing-resistant authentication using PAPE. Feel free to use it for testing.
PAPE allows sites that use OpenID 2.0 authentication to get information about the way that the user authenticated to the provider. This is an important step on the way to getting the convenience needed of OpenID authentication for higher-valued transactions. It’s trivial to implement and will be included in JanRain’s OpenID 2.0 libraries as well as Sxip’s libraries.
Gary Krall also added that:
Verisign will also be releasing an update to the JOID library which we use on the PiP for as you may know we have added PAPE support to the PiP.
And I’ll add that MyOpenID.com and SignOn.com both also support PAPE on their OpenID providers.
Why is this exciting? Because it means that without use of without any use of passwords, people can create and use OpenIDs with their Information Cards. And that sites accepting OpenIDs can ask for phishing-resistant authentication when you sign in — which these OpenIDs will do for you. All more great steps towards building a convenient, secure, ubiquitous identity layer for the Internet!
 As Scott Kveton just posted, earlier this month the OpenID Foundation board approved OpenID Intellectual Property Policy and Procedures documents. These are designed to achieve two goals:
As Scott Kveton just posted, earlier this month the OpenID Foundation board approved OpenID Intellectual Property Policy and Procedures documents. These are designed to achieve two goals:
 I was surprised during the
I was surprised during the