 Last week IDology demonstrated a first that many of us see great possibilities for: an Information Card making a verified age claim. I’m excited at this first step towards the goal of enabling people to routinely use interoperable verified claims about themselves via Information Cards.
Last week IDology demonstrated a first that many of us see great possibilities for: an Information Card making a verified age claim. I’m excited at this first step towards the goal of enabling people to routinely use interoperable verified claims about themselves via Information Cards.
Obtaining my age-verified card online was easy. I submitted my name, address, and birth date (via a self-issued card) to IDology’s verification process. Next they asked me a few additional questions to confirm that I was likely to be the person who I claimed to be. With correct answers in hand, they proceeded to issue me an Information Card enabling me to make IDology-verified claims on my own behalf.
I used the card at two (demo) relying parties: a social networking site that restricts membership to people 18 and over and an online wine store. You can also imagine verified identity information being valuable at job and career sites, at dating sites, when applying for insurance or credit, for enrolling in promotions, etc. The possibilities are endless.
Please join me in congratulating IDology on this significant achievement. I believe it will be the first of many good things to come in the verified identity space!
The remainder of this post shows the process of obtaining and using my verified identity Information Card. In some cases I intentionally went through extra steps, such as previewing the cards before sending them, to make it completely clear what is occurring. The address of the demo site is obscured at IDology’s request because this is not yet a production service. Some of the (real) data about me used to obtain the card is obscured for privacy reasons.
Signing Up for a Verified Age Card
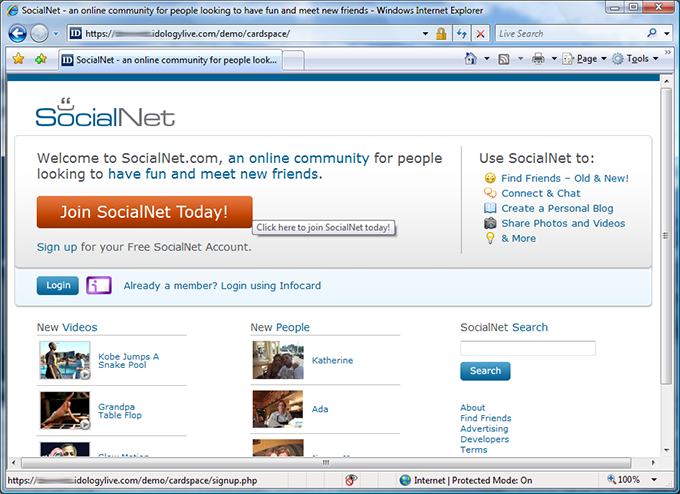
The experience starts by visiting the “SocialNet” site, which invites me to join. I click “Join SocialNet Today”.
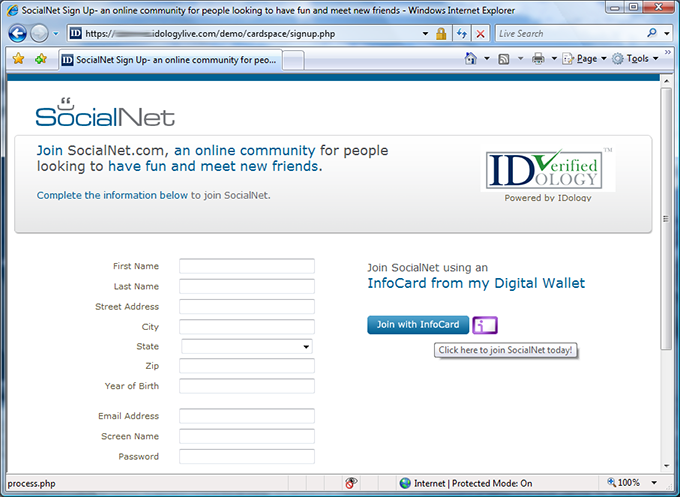
SocialNet lets me join either by typing my information into a web form or by providing it via an Information Card. I click the Information Card icon.
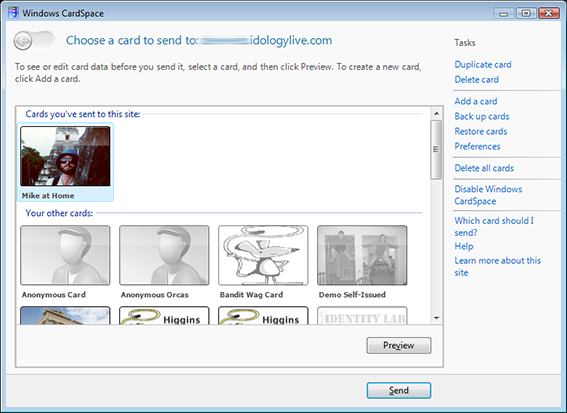
This brings up CardSpace, where I choose a self-issued card with my home address.
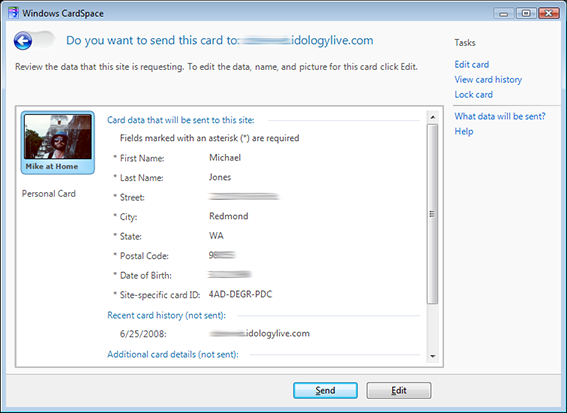
I preview the card, seeing that the site will be sent my name, address, and birth date. I click “Send”.
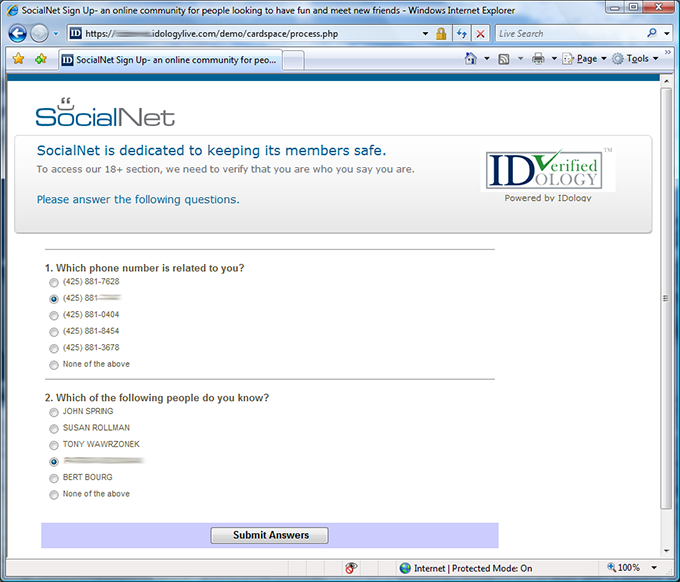
I’m asked two questions that I should know the answers to to help confirm that I am who I say I am. I answer them correctly.

Having passed the identity verification process, I’m given the opportunity to download an Information Card for my newly verified identity. I click on “Download Managed InfoCard”.
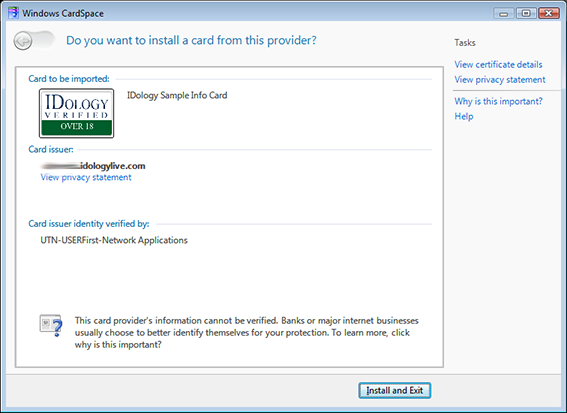
I click the “Install and Exit” button to install my verified identity Information Card.
Using the Card at SocialNet
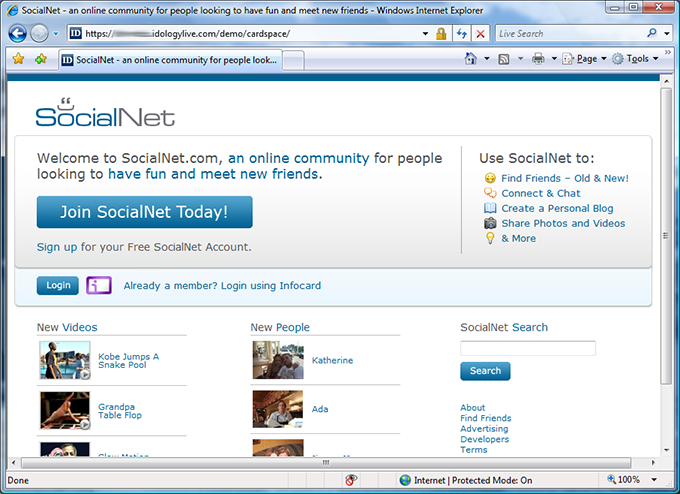
Now that I have a verified age card, I use it to sign in at SocialNet by clicking on the Information Card icon.
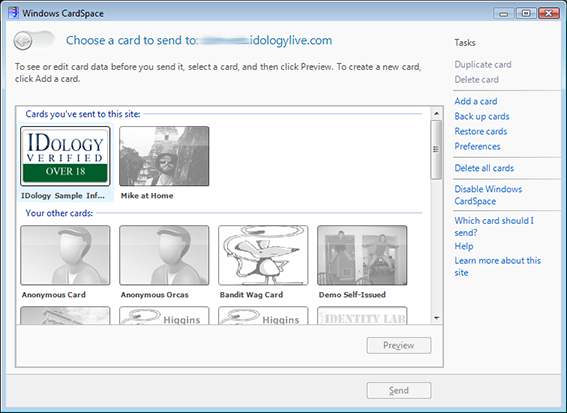
I choose my IDology verified Information Card and click “Preview” to review the claims I’m being asked for.
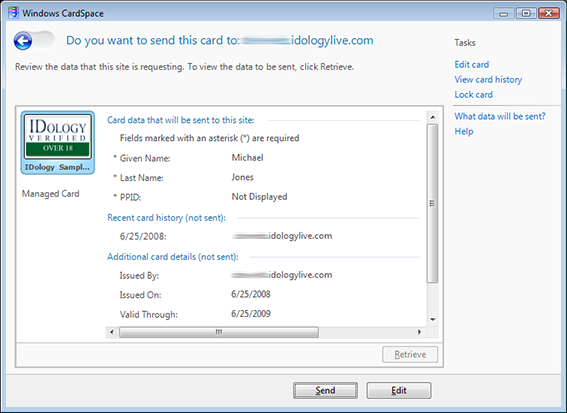
SocialNet is only asking for my name and the PPID for my card. I send them.
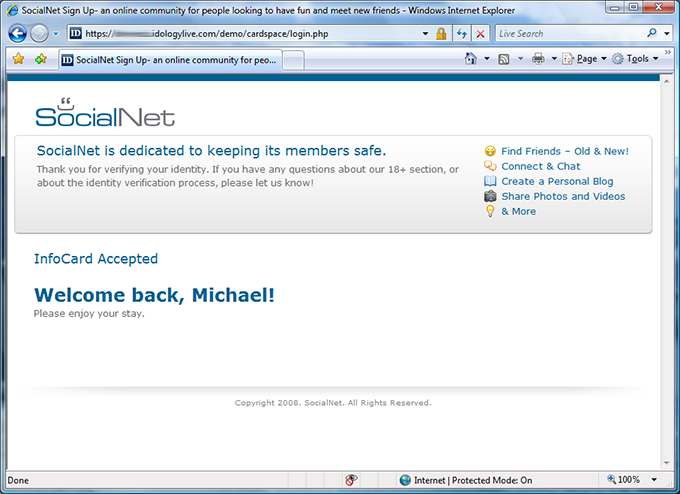
I’m logged into SocialNet using my verified Information Card.
Using the Card at OnlineWineMerchant.com
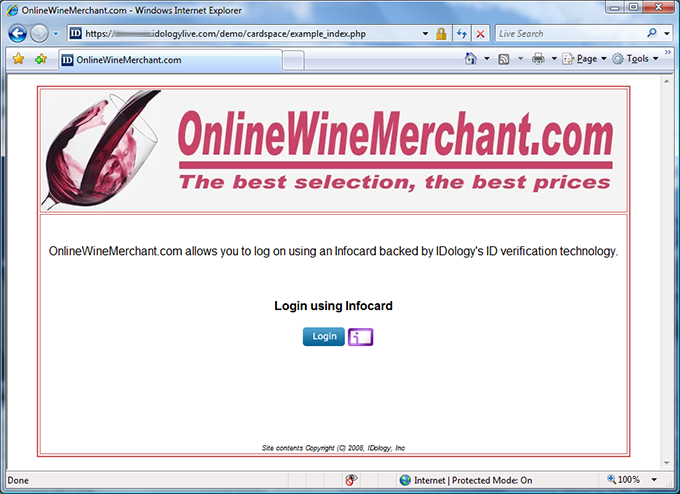
Now I go to another site that accepts my verified age Information Card: “OnlineWineMerchant.com”. I click the Information Card icon to sign in.
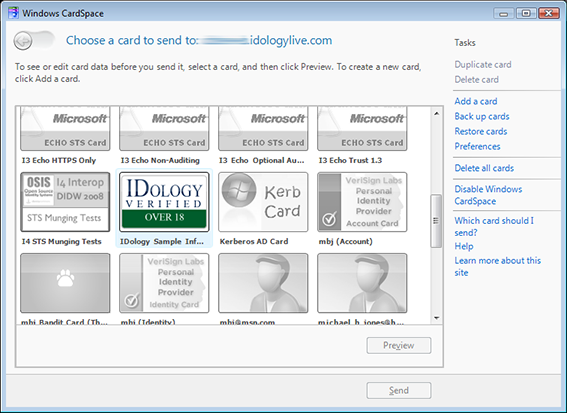
My IDology verified Information Card is accepted by the site. I choose it and click “Preview”.
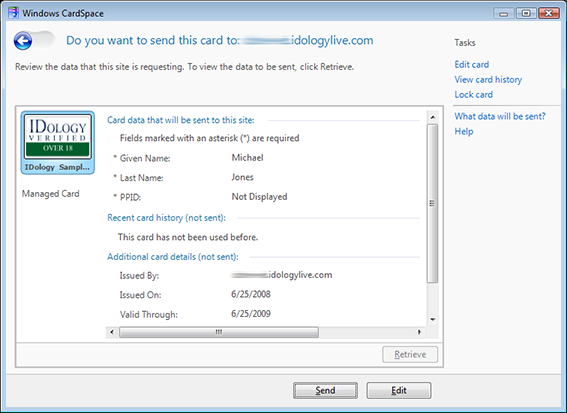
OnlineWineMerchant.com is also only asking for my name and a PPID. (In a real deployment, I suspect it would be asking for an age claim of some kind too.) I send the card.
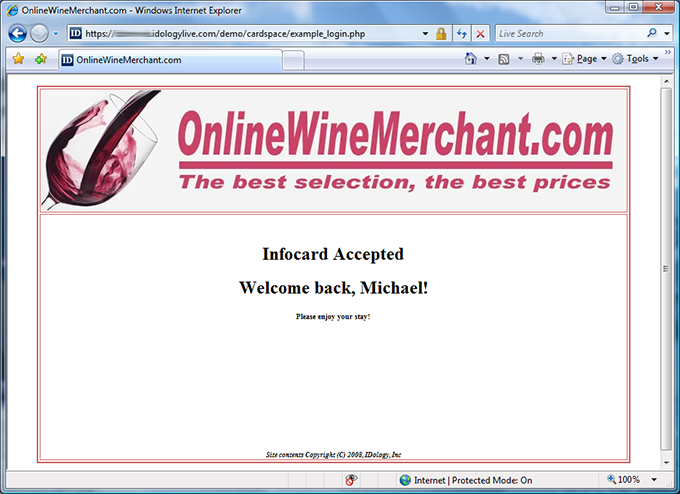
I’m logged into OnlineWineMerchant.com using my verified age card, letting me take advantage of the verification I did for SocialNet on this site too. This is the synergy that will make Information Cards with verified identity claims a valuable addition to the identity landscape.
 Microsoft recently created a Consumer Website for CardSpace to educate end-users about Windows CardSpace and Information Cards. This complements the developer-focused information at the MSDN CardSpace site and the CardSpace Community Site.
Microsoft recently created a Consumer Website for CardSpace to educate end-users about Windows CardSpace and Information Cards. This complements the developer-focused information at the MSDN CardSpace site and the CardSpace Community Site.
 Last week
Last week 















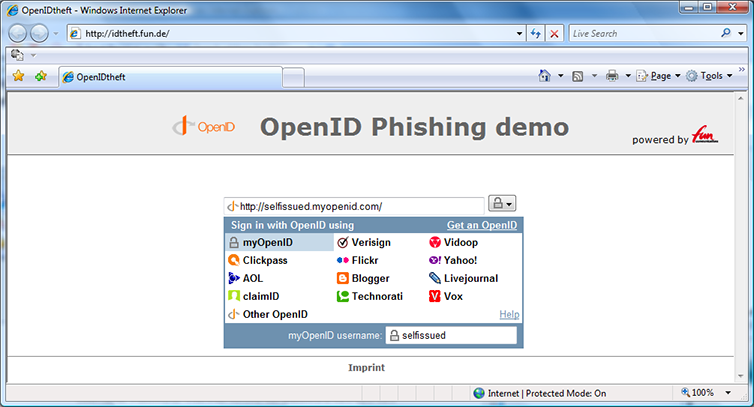
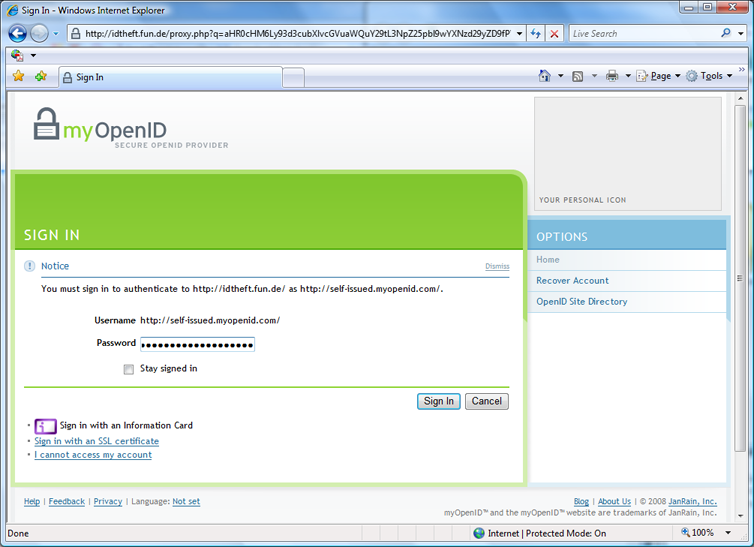
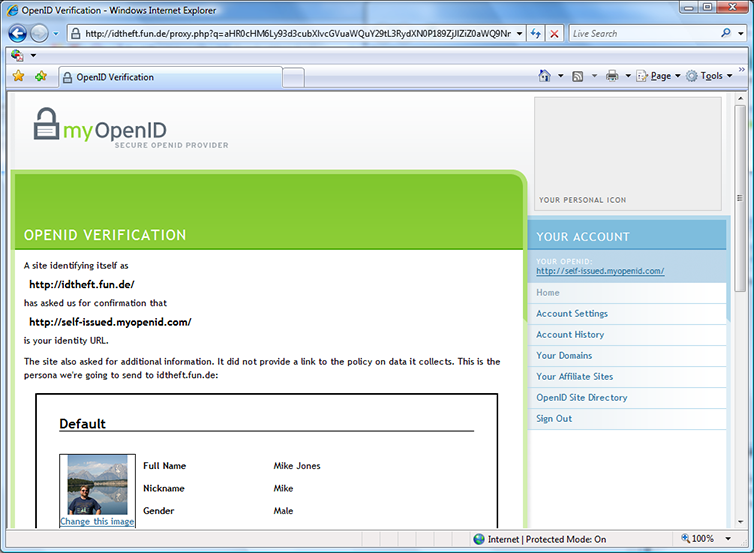
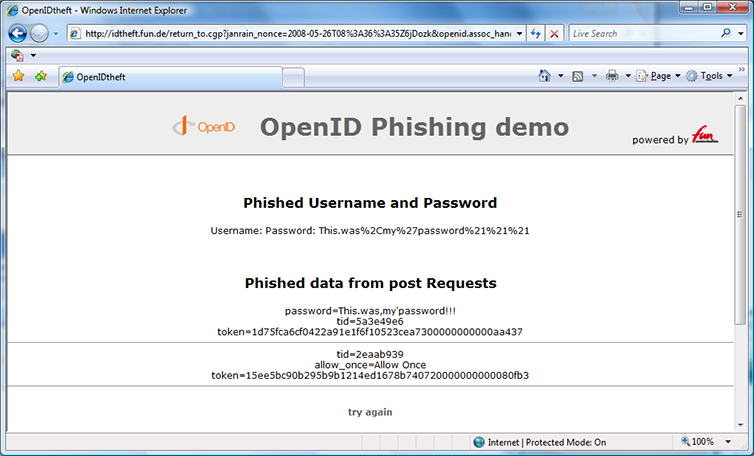
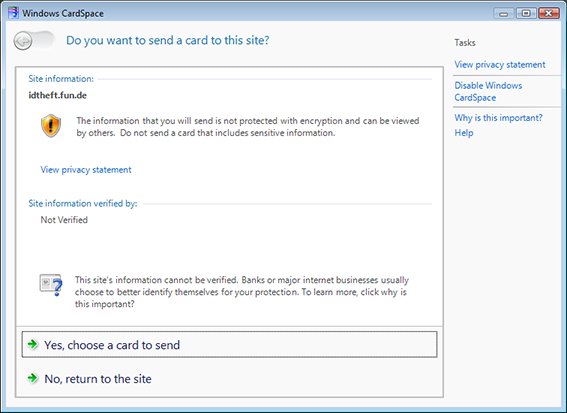
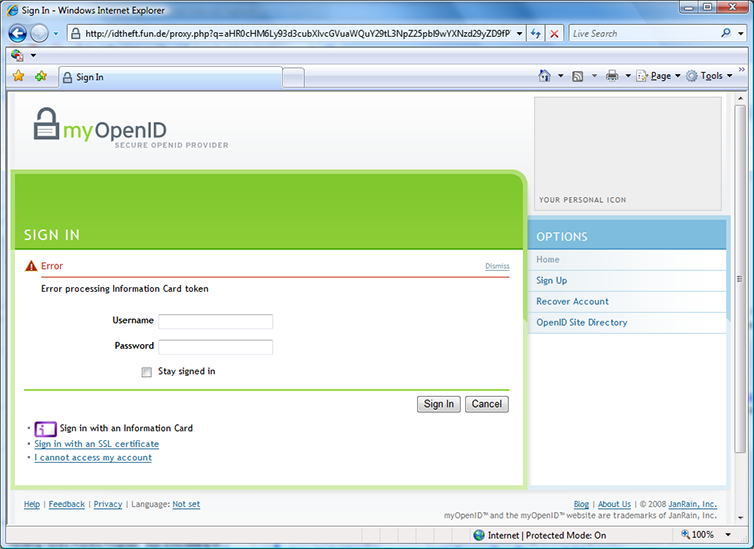

 I recently encountered
I recently encountered 
 I’m writing today to publicly welcome
I’m writing today to publicly welcome 
 I’m pleased to announce that the .NET Framework 3.5, which includes a new version of Windows CardSpace, is now
I’m pleased to announce that the .NET Framework 3.5, which includes a new version of Windows CardSpace, is now  I’ve been inspired by Kim’s
I’ve been inspired by Kim’s 
 This week the public pilot of the healthcare portal
This week the public pilot of the healthcare portal