Kim and I had fun with this video but we’re seriously pleased to be able to show you both using LiveID with Information Cards and DigitalMe in action together. Check it out!
Author: Mike Jones Page 32 of 33
Building the Internet's missing identity layer
Today Andy Hodgkinson announced a binary release of the DigitalMe Identity Selector for Mac OS X. Now Mac users can use Information Cards with just a drag-and-drop install! This release builds upon the earlier success of their binary release for SuSE Linux.
As Andy wrote: “I would encourage anyone interested in using information cards on the Mac to install DigitalMe and the Firefox plug-in.” I’ll second that. Go check it out!
Congratulations again to the Bandit team!
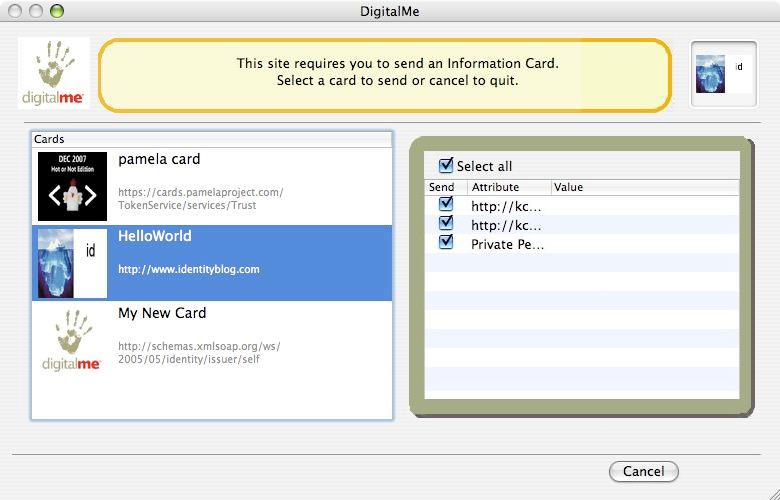
The Windows LiveID team just added beta support for signing into your Windows LiveID accounts with self-issued Information Cards. Now I read my hotmail without ever typing a password. Very cool!
This post announced the support:
Windows Live ID adds Beta support for Information Cards with Windows CardSpace!
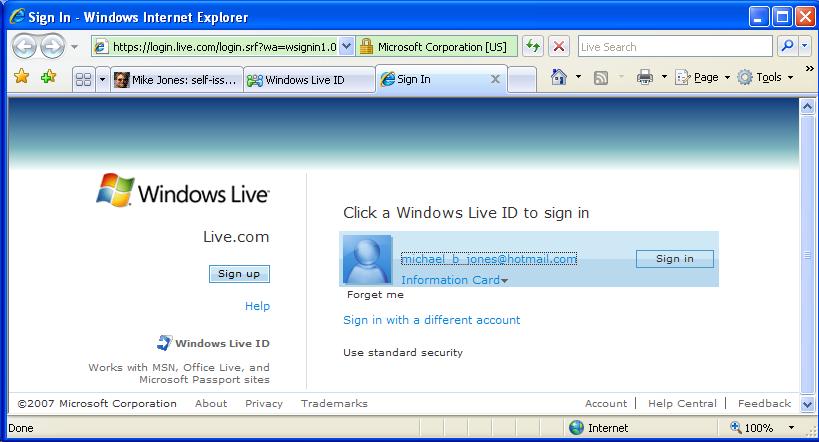
Windows CardSpace is a new way to sign in securely and conveniently into websites. And now you can use CardSpace with your Windows Live ID account! Using CardSpace with Windows Live ID means you don’t use a password to sign-in. Instead, just send your Information Card to Live ID to identify you and get signed into Hotmail, Windows Live Spaces or any other site that accepts Windows Live ID. And it is incredibly easy to use CardSpace with your Live ID. Just follow this link (here) to get going in minutes!
If you are using Windows Vista, you are all ready to use CardSpace! If you are on Windows XP or Windows 2003, you will need to get IE 7.0, our newest and coolest browser and .Net 3.0 with CardSpace support (if you don’t already have them). You will also need to add an Information Card to your Live ID account. To install these components and add an Information Card to your Live ID account, visit the Windows Live ID Information Card management page. Also go to that page to make changes to the Information Card added to your Live ID account.
Once you’ve added an Information Card to your Live ID account, sign in using the Information Card. You will be amazed at how easy it is! BTW, that Windows Live ID CardSpace support is still a “Beta”. We are still working on it and know a bunch of things that could be better. But do let us know your wish list; it is always good to get feedback.
Nayna Mutha, Program Manager – LiveID
Rob Franco, Lead Program Manager – Windows CardSpace
Here’s what it looks like:
Congratulations to the LiveID team for helping make the web safer and easier to use!
Sxip Identity just finished a draft specification that enables a really useful form of convergence between OpenIDs and Information Cards: presenting your OpenID as an Information Card you select rather than as a string you type. Johnny Bufu’s OpenID general mailing list note introduces this specification for community review.
This combination has several advantages over standard OpenID usage. First, there’s no OpenID string to type when you use your OpenID, which should make OpenIDs easier for more people to use. Second, this is a phishing-resistant authentication method. Finally, it lets you recognize and choose your OpenID visually, based on the card graphics supplied by the OpenID provider.
Sxip also backed this specification by a sample implementation, which you can check out at https://openidcards.sxip.com/. Now for some more details….
Here’s how it works: In this model, the OpenID relying party asks for an OpenID Information Card using an object tag on the page rather than having the user type the OpenID as a string (while probably also giving the user the option to instead type in the string for backwards compatibility). The user’s Identity Selector then lets the user choose which OpenID card to send to the site. The card transmits the actual OpenID string to the site as a claim. From that point on, standard OpenID protocol interactions ensue.
For instance, the sample relying party page asks you to “Login with an OpenID InfoCard” and requests the card using this evocative graphic:

Upon clicking the graphic, my identity selector is invoked, which shows me that I can use this OpenID Information Card at the site (which I’d previously obtained here):

After that, the sample performed a standard OpenID attribute exchange and the relying party greeted me with:
Welcome! You have logged in using your https://openidcards.sxip.com/i/mbj OpenID identifier.
Phone: (omitted)
Country: USA
Email: mbj@microsoft.com
City: Redmond
Address: One Microsoft Way, Building 40/5138
LastName: Jones
FirstName: Mike
Behind the scenes, the relying party had received this OpenID assertion:
<openid:OpenIDToken xmlns:openid="http://specs.openid.net/auth/2.0">openid.ns:http://specs.openid.net/auth/2.0
openid.op_endpoint:https://openidcards.sxip.com/op/
openid.claimed_id:https://openidcards.sxip.com/i/mbj
openid.response_nonce:2007-08-26T20:55:34Z0
openid.mode:id_res
openid.identity:https://openidcards.sxip.com/i/mbj
openid.return_to:https://openidcards.sxip.com/demorp/
openid.assoc_handle:f27d249fc4108198
openid.signed:op_endpoint,claimed_id,identity,return_to,response_nonce,assoc_handle
openid.sig:gKKpDjEbgByJo48Q800Jq4gCJng=
openid.ns.ext1:http://openid.net/srv/ax/1.0-draft4
openid.ext1.mode:fetch_response
openid.ext1.type.attr1:http://axschema.org/contact/phone/default
openid.ext1.value.attr1:(omitted)
openid.ext1.type.attr2:http://axschema.org/contact/country/home
openid.ext1.value.attr2:USA
openid.ext1.type.attr3:http://axschema.org/contact/email
openid.ext1.value.attr3:mbj@microsoft.com
openid.ext1.type.attr4:http://axschema.org/contact/city/home
openid.ext1.value.attr4:Redmond
openid.ext1.type.attr5:http://axschema.org/contact/postalAddress/home
openid.ext1.value.attr5:One Microsoft Way, Building 40/5138
openid.ext1.type.attr6:http://axschema.org/namePerson/last
openid.ext1.value.attr6:Jones
openid.ext1.type.attr7:http://axschema.org/namePerson/first
openid.ext1.value.attr7:Mike
</openid:OpenIDToken>One final technical note that will be of interest to some of you: OpenID Information Cards do not use SAML tokens. They use one of two variants of openid:OpenIDToken tokens (depending upon whether the OpenID relying party uses OpenID 1.1 or 2.0 authentication).
Go get yourself an OpenID Information Card and give it a spin! Read and comment on the spec. Or even better yet, implement it and tell us about your experience!
 An updated version of the Information Card Deployment Guide is now available. Among other improvements, it’s been updated to employ the Information Card Icon. As the original deployment guide announcement said:
An updated version of the Information Card Deployment Guide is now available. Among other improvements, it’s been updated to employ the Information Card Icon. As the original deployment guide announcement said:
So you’ve decided to use Information Cards on your web site… Now what? I’m pleased to announce that we’ve just published a document giving step-by-step guidance to Web developers on what we believe are the best practices for doing this. The document walks Web site developers through two different deployment scenarios: sites exclusively using Information Cards for authentication, and mixed-mode sites allowing the use of either passwords or Information Cards. Examples are given for site sign-in, site sign-up, and handling lost Information Cards, including suggested confirmation text for each of these scenarios.
This link to the document Patterns for Supporting Information Cards at Web Sites: Personal Cards for Sign up and Signing In references the current version and will be updated to point to any future revisions as well. The Sample Information Card Site employs these guidelines and is built using the Information Card Relying Party Resources announced earlier. Enjoy adding Information Card support to your web sites!

I’ve been waiting to write about the user-centric identity interop at the Burton Group Catalyst conference until the Burton Group report about the event was published. Now it’s here!
At the interop we demonstrated interoperability between 7 Identity Selectors, 11 Identity Providers, and 25 Relying Parties. As Bob Blakley wrote:
The interop event was a milestone in the maturation of user-centric identity technology. Prior to the event, there were some specifications, one commercial product, and a number of open-source projects. After the event, it can accurately be said that there is a running identity metasystem.
The full report includes a list of participants and the software they brought to the table, an overview of the results achieved, as well as the issues identified through the interop. See Bob’s post for all the details!
The report also includes thank-yous, to which I’d like to make some additions: Thanks are due to Jamie Lewis, Gerry Gebel, and Bob Blakley of the Burton Group for sharing our vision for this interop, striving to make it the best that it could be, and tirelessly working the details until it came true. You truly helped the industry to come together in a valuable and significant way.
Also, while I appreciate Bob’s thanks for the work I put into the Open Specification Promise, there were many believers in and drivers of this important work at Microsoft besides myself, both from the Law and Corporate Affairs team and from the Federated Identity product group. This was truly a team effort.
I’m also happy to report that there will be a follow-on interop in Europe at the Catalyst conference in Barcelona, October 22-25, which will hopefully include even more participants and scenarios, including more multi-protocol interoperation proof points. Hope to see you there!
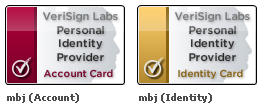 This week VeriSign upgraded their Personal Identity Provider (PIP) to support Information Cards. As David Recordon wrote at VeriSign’s official “Infrablog”:
This week VeriSign upgraded their Personal Identity Provider (PIP) to support Information Cards. As David Recordon wrote at VeriSign’s official “Infrablog”:
Last Saturday, we completed the upgrade of our Personal Identity Provider. All accounts have been automatically upgraded and the URL is the same at http://pip.verisignlabs.com. We definitely encourage everyone to come try it out as we believe it is the best OpenID Provider in existence! Not only does it have all of the features from the PIP we launched last May, but adds support for OpenID 2.0, the ability to manage multiple identities within one PIP account, integration with strong authentication via our VeriSign Identity Protection network, Information Card support as one way to help protect against phishing attacks, and our SeatBelt Firefox add-on which works with a variety of OpenID Providers.
PIP supports Information Cards in two ways:
- Logging into your PIP account: You can use a managed Information Card to log into your PIP account, providing a phishing-resistant alternative to logging in with a username and password typed into the browser.
- Using your PIP Identities at other sites: PIP issues managed Information Cards for each of your PIP identities, which you can use to sign into sites using Information Cards for login and/or account creation. (And of course, these same identities are also OpenIDs as well.)
Images of my PIP cards for these two use cases are shown at the top of this post. I can now use my PIP account card to sign into my PIP account and my PIP identity card to sign into other sites. PIP is doubly cool because I believe it’s also the first general-purpose identity provider to be secured by an Extended Validation Certificate (see the green color of the IE7 address bar?). Great progress!
 This follows on last month’s launch of Ping Identity’s SignOn.com identity provider. SignOn.com lets you log into your OpenID account using a self-issued Information Card — a convenient, password-free, and phishing-resistant authentication mechanism.
This follows on last month’s launch of Ping Identity’s SignOn.com identity provider. SignOn.com lets you log into your OpenID account using a self-issued Information Card — a convenient, password-free, and phishing-resistant authentication mechanism.
Both are fantastic steps towards our shared goal of building a convenient, secure, ubiquitous identity layer for the Internet. Expect to see lots more developments like this soon!
Yours truly,
mbj.pip.verisignlabs.com and mbj.signon.com
 Let me second Scott Kveton‘s congratulations to David Recordon for winning this year’s Google-O’Reilly Open Source award for Best Strategist. As Scott wrote:
Let me second Scott Kveton‘s congratulations to David Recordon for winning this year’s Google-O’Reilly Open Source award for Best Strategist. As Scott wrote:
Tonight, David Recordon of Verisign won Google’s prestigious “Best Strategist” open source award for his work on OpenID.
I’ve known David for a little over a year and have been amazed at hist ability to help shape the technology and community that makes up OpenID (all this before the ripe old age of 21 … no congratulatory beers for you David!).
I first met David during a meeting at Six Apart (long, long ago) with he and Brad (the creator of OpenID) when we all cooked up the OpenID Bounty program. I was a newbie in the OpenID world and David was great at helping me as I found my way.
David has been tireless in his work on OpenID being “the face” of the community and spending more time on the road than anybody I’ve ever seen (c’mon, the guy is already a United uber frequent flyer) showing up at every conference you can think of across the entire globe. He has been instrumental in seeding small user communities across the globe with his passion for making OpenID the technology it has become.
David, you have a fantastic future ahead of you … congrats, the best is yet to come.
I’ve also greatly enjoyed working with David on advancing digital identity together over the past year and value his energy, judgment, and fun-loving spirit. I’ll see you out there on the Identity road, David… Congratulations again!
 The first CardSpace book, Marc Mercuri‘s Beginning Information Cards and CardSpace: From Novice to Professional went to press last week and can now be ordered. Marc is an expert in CardSpace and numerous related technologies and his book is chock full of practical examples and samples. Read more about Marc here. Another CardSpace expert, virtual team member, and friend of mine, Steven Woodward, served as technical editor for the book. Congratulations Marc and Steven!
The first CardSpace book, Marc Mercuri‘s Beginning Information Cards and CardSpace: From Novice to Professional went to press last week and can now be ordered. Marc is an expert in CardSpace and numerous related technologies and his book is chock full of practical examples and samples. Read more about Marc here. Another CardSpace expert, virtual team member, and friend of mine, Steven Woodward, served as technical editor for the book. Congratulations Marc and Steven!
In a recent comment, midtoad wrote:
There appears to be no way possible to allow my browser to recognize or use CardSpace cards. The one-minute video mentions a small download to be provided but none are available.
Let me try to help here. If you’re on Windows XP or Windows Server 2003 and you want to use Windows CardSpace you need to:
- Upgrade to Internet Explorer 7, which you can do with Windows Update.
- Install the .NET Framework 3.0, either as one of the optional installations available via Windows Update or from this downloadable package (as advertised on the cover page of http://www.netfx3.com/).
(Of course, if you’re on Windows Vista, you already have both.)
Finally, you didn’t say what browser you’re using. If you’re using IE you’re already set. If you’re using Firefox, follow the installation instructions at http://www.perpetual-motion.com/. And if you’re on other platforms, you might want to check out the Bandit Project’s DigitalMe downloads. Hope this helps!
At http://www.cardspacedemos.com/FriendsWithCards/ you can try out a web site that uses Information Cards for account creation and site sign-in. It also allows you to create an account in the old way, with a username and password, and then associate Information Cards with that account. This site is intended to enable you to experience a site using Information Cards that you can use as a model for the flows on your site.
This site simulates e-mail address verification upon account creation. This enables “lost card” scenarios to be handled via card reset e-mails, similarly to how “lost password” scenarios are often handled today. I write “simulated”, because the site doesn’t actually send the e-mails — it just presents the bodies of the e-mails that would be sent as web pages.
This site is built using the Information Card Relying Party Resources I wrote about last week and follows the guidance in the Information Card Deployment Guide. I hope you will find this site useful to further your understanding of how to best employ information cards at your site.
Of course, site best practices are still a work in progress that others are helping to evolve as well, so I’d love to hear feedback on what you like at this site and what you think can be improved. For instance, Eric Norman correctly points out a place where the current site needs to be improved. The My Account page at SignOn.com already does a much better job here, identifying your cards by displaying your name and e-mail address, rather than an unintelligible string of characters. Keep those good ideas coming!
Let me be the first to congratulate the Bandit and Higgins project members on the release of the DigitalMe Identity Selector for SuSE Linux! Now, for the first time, Linux users have an installable Identity Selector available to them that enables them to use Information Cards in a way that’s compatible with Windows CardSpace. See Novell’s press release “Bandit Project’s Cross-Platform Card Selector Gives Users Control of their Internet Identities“, the Identity Selector Service page, and the Identity Selector Service Download page for more details.
This announcement lets people who aren’t developers start to use Information Cards on Linux and builds on the interoperability successes demonstrated at Brainshare. And as the downloads page says, “Work is under way to provide packages for other Linux distros, OS X and Windows.” Great stuff!
Congratulations again!
Today Microsoft released two related code samples for Information Card relying parties: the Information Card Kit for HTML and the Information Card Kit for ASP.NET 2.0.
The HTML kit is platform-independent JavaScript and CSS code that can be used to dynamically detect client Information Card support and tailor the web site’s interactions with the user accordingly. If Information Cards are supported, this code will request an Information Card for the site. Utility code included can also be used to display passive notifications. Additional code will be required at the server to consume the security token sent by the user. Download the HTML kit here.
The Information Card Kit for ASP.NET 2.0 contains code that can be used on the ASP.NET 2.0 platform to accept Information Cards. This code enables the server to consume the security token delivered to the server when the person uses an Information Card. Download the ASP.NET 2.0 kit here.
![]() I’m very pleased to announce that, as of today, there is now a graphical icon freely available for people to use to indicate that “Information Cards are accepted here”. This icon is intended to provide a common visual cue that Information Cards can be used to provide information to a site or program, similarly to how the RSS icon
I’m very pleased to announce that, as of today, there is now a graphical icon freely available for people to use to indicate that “Information Cards are accepted here”. This icon is intended to provide a common visual cue that Information Cards can be used to provide information to a site or program, similarly to how the RSS icon ![]() is used to indicate the availability of syndicated content.
is used to indicate the availability of syndicated content.
The guidelines for the use of the icon, a frequently asked questions document, a set of png images of the icon rendered in a range of sizes, and the original artwork in Illustrator format are all available together in a download package. Please consult the guidelines and the FAQ before using the icon.
You’ll notice that the login page for my blog now uses the icon. Hopefully your sites will soon too!
And just for fun, because the icon is, after all, a graphical element, here’s a gallery of the renderings of the icon that we included in the downloads package. Enjoy!
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Great news from Pat Patterson of Sun Microsystems about support for WS-Federation now being checked into the OpenSSO project:
The WS-Federation service provider and configuration CLI code was committed into OpenSSO yesterday – this PDF gives some basic instructions on getting started with WS-Fed and OpenSSO. Note that this is just the initial drop of code – still to come is identity provider support.Give it a whirl and send us feedback at dev(at)opensso.dev.java.net.
David Recordon just posted a simple draft OpenID specification enabling OpenID relying parties to request that a phishing-resistant authentication method be used by the OpenID provider and for providers to inform relying parties whether a phishing-resistant authentication method, such as Windows CardSpace, was used. This is a major step forward in fulfilling the promise of the JanRain/Microsoft/Sxip Identity/VeriSign OpenID/Windows CardSpace collaboration announcement introduced by Bill Gates and Craig Mundie at the RSA Security Conference this year.
In his post “Bringing Useful Scalable Security to OpenID” David wrote:
The integration cost of OpenID as a Relying Party is extremely low, the technology is free and as Brian Ellin and I showed at Web 2.0 Expo the time commitment is also low due to a lot of great Open Source code out there which takes care of the heavy lifting. So now the RP has successfully integrated OpenID and removed the need for new users to create yet another password for their site, though they no longer have the control over the strength of a user’s authentication process. The RP may be a simple Web 2.0 site and not care beyond that the user has a password, it may store marginally sensitive information and want to make sure that the Provider did something to help protect the user from common phishing attacks, or maybe it’s a site which has truly sensitive information and wants to make sure that a second-factor device, such as a VIP token, was used.
With the OpenID Provider Authentication Policy Extension that I just published, this is now possible. This extension to OpenID 1.1 and 2.0 allows Relying Parties to express preferences around the authentication, such as “use technology which is phishing resistant” (stemming from the collaboration announcement at the RSA conference earlier in the year), for the Provider to inform the user of the request, guide them through the authentication process, and then inform the Relying Party what happened. By taking advantage of existing specifications from the likes of the National Institute of Standards and Technology (NIST), Providers can also convey information as to the strength of a password or combination of a password and digital certificate or hardware device used. While the high-end of the specification may be beyond the uses of OpenID today, it certainly fulfills the scalable security vision that we have. Through this specification not only can I now strongly protect my OpenID identity, but let others know that I’m doing so and truly take advantage of a reduction in credentials needed when browsing the web.
I can’t wait to use the implementations that are sure to follow shortly!
Which would you trust more? Self-issued claims or unverified claims?
Read Marc Goodner’s new blog and decide for yourself. ;-)
Don Schmidt recently posted this valuable entry announcing the publication of the IBM/Microsoft whitepaper “Understanding WS-Federation“:
Yesterday a White Paper, Understanding WS-Federation, was jointly published by IBM and Microsoft. The primary goal of this paper is to promote an appreciation for the functional scope of the revised publication of WS-Federation. As I have stated in previous posts, the scope of this specification extends far beyond the features delivered in first generation WS-Federation products, such as, Active Directory Federation Services v1.
The paper includes two use cases, an Enterprise “request for proposal” scenario and a Healthcare “emergency room treatment” scenario, that highlight key new features of WS-Federation 1.1. Textual descriptions of the scenarios are annotated with sample XML message flows.
Another goal of this paper is to encourage participation in the OASIS WSFED TC. Hopefully WS-Federation supporters and critics, alike, will find functionality that they care about, and be wiling to join in the open standards process for WS-Federation 1.1.
Very valuable reading for anyone wanting to understand the capabilities of WS-Federation, its relationship to WS-Trust, and the Security Token Service (STS) model.
And then in Don’s classic gracious style, he wrote the post “Standing on the Shoulders of Giants“, giving credit where credit is due, and asking for broad community participation in the OASIS WSFED TC. I highly recommend it as well.
On Tuesday afternoon at IIW representatives from numerous Information Card projects sat down at the same table (actually, 3 tables so we would all fit :-) ) and systematically used our implementations together, exercising the different possible combinations. The session notes, as posted on the OSIS wiki, tell the story:
Notes from IIW 2007a
The OSIS group sponsored an Information Card interoperability connect-a-thon on May 15, 2007 as part of the Internet Identity Workshop 2007 A in Mountain View California. Participants collaborated to work through combinations of Identity Provider, Identity Agent, and Relying Party scenarios, in order to identify and workshop problems with interoperability. The following representatives were present and participated:
5 Information Card Selectors
- Ian Brown’s Safari Plugin
- XMLDAP
- Windows Cardspace
- Higgins IdA Native
- Higgins IdA Java
11 Relying Parties
- Bandit (basic wiki authentcation)
- Bandit (elevated privileges)
- PamelaWare
- CA
- XMLDAP
- Windows Live RP (used to obtain a managed card)
- Windows Live/single-issuer (where you can use the managed card)
- Oracle RP
- Identityblog RP (based on Rob Richards’ library)
- Identityblog helloworld token RP
- UW/Shibboleth
7 Identity Providers
- Higgins
- Bandit
- XMLDAP
- UW/Shibboleth
- LiveLabs
- HumanPresent
- Identityblog HelloWorld IdP
4 Token Types
- SAML 1.0
- SAML 1.1
- helloworld
- username token
2 Authentication Mechanisms
- username/password
- self-issued (personal) card
Many combinations interoperated as expected; several issues were identified and are being fixed in preparation for the coming Information Card Interop event to be held at the Burton Group Catalyst Conference in San Francisco (June 25-29).
One of the things I love about IIW is that it’s a working meeting — not a series of mind-numbing presentations. This interop was a great example of the industry coming together and doing work together. And of course, this session was a dry run for the upcoming User-Centric Identity Interop event coming at Catalyst next month, where even more projects will be represented. Hope to see many of you there!
Today at the Interop Conference in Las Vegas, Bob Muglia announced Microsoft’s sponsorship of four open source projects that are producing Information Card Relying Party software for important web programming environments: Ruby on Rails, Java, PHP, and C. The press release, which also talks about extending the Open Specification Promise to the Information Card Specifications, contains supportive quotations from several friends in the identity community: Paul Trevithick and Mary Ruddy, Tony Nadalin, Dale Olds, and Gerry Gebel.
Details on the Ruby and Java projects were announced, with details on the PHP and C projects to follow. See these sites for details:
Ruby on Rails Relying Party:
http://rubyforge.org/projects/informationcard/
http://www.codeplex.com/informationcardruby
Java Relying Party:
http://sourceforge.net/projects/informationcard/
http://www.codeplex.com/informationcardjava

