 In October, Microsoft announced that Windows Live IDs would also be OpenIDs. Today the Live ID team published an analysis of what we have learned in operating the Community Technology Preview (CTP) release of our OpenID provider. The post is well worth read and covers, among other things, lessons learned about aliasing and namespaces, having multiple ways to reach the same functionality, and explaining things to users. Enjoy!
In October, Microsoft announced that Windows Live IDs would also be OpenIDs. Today the Live ID team published an analysis of what we have learned in operating the Community Technology Preview (CTP) release of our OpenID provider. The post is well worth read and covers, among other things, lessons learned about aliasing and namespaces, having multiple ways to reach the same functionality, and explaining things to users. Enjoy!
Author: Mike Jones Page 28 of 33
Building the Internet's missing identity layer
![]()
 I’m thrilled to announce that the Identity Metasystem Interoperability Version 1.0 specification has been approved as an OASIS standard, with 56 votes in favor and none against. This standard benefitted substantially from the input received during the process. Numerous clarifications were incorporated as a result, while still maintaining compatibility with the Identity Selector Interoperability Profile V1.5 (ISIP 1.5) specification.
I’m thrilled to announce that the Identity Metasystem Interoperability Version 1.0 specification has been approved as an OASIS standard, with 56 votes in favor and none against. This standard benefitted substantially from the input received during the process. Numerous clarifications were incorporated as a result, while still maintaining compatibility with the Identity Selector Interoperability Profile V1.5 (ISIP 1.5) specification.
While this is often said, this achievement is truly the result of a community effort. While by no means a comprehensive list, thanks are due to many, including the OSIS members whose diligent efforts ensured that Information Cards are interoperable across vendors and platforms, the Information Card Foundation members for their adoption and thought leadership work, and the IMI TC members, including co-chairs Marc Goodner and Tony Nadalin, and Mike McIntosh, who was my co-editor. Paul Trevithick and Mary Ruddy get enormous credit for starting and leading the Higgins Project, as does Dale Olds for the Bandit Project. Kaliya Hamlin and Phil Windley were instrumental behind the scenes by running the IIWs. Axel Nennker has been a tireless force, producing both ideas and software, as has Pamela Dingle. Jamie Lewis, Bob Blakley, and Craig Burton all provided insightful guidance on the practical aspects of birthing a new technology. Arun Nanda deserves enormous thanks for doing the heavy lifting to produce the ISIP 1.0 spec. And of course, none of this would have occurred without the leadership and vision of Kim Cameron. Thanks one and all!
![]()
 OASIS has scheduled the standards approval vote for the Identity Metasystem Interoperability Version 1.0 specification for June 16-30. My thanks to everyone who submitted comments during the public review. Numerous clarifications have been incorporated as a result of your comments, while still maintaining compatibility with the Identity Selector Interoperability Profile V1.5 (ISIP 1.5) specification.
OASIS has scheduled the standards approval vote for the Identity Metasystem Interoperability Version 1.0 specification for June 16-30. My thanks to everyone who submitted comments during the public review. Numerous clarifications have been incorporated as a result of your comments, while still maintaining compatibility with the Identity Selector Interoperability Profile V1.5 (ISIP 1.5) specification.
Microsoft announced the availability of the second beta of its forthcoming “Geneva” claims-based identity software today during Tech•Ed. This is a significant milestone for the team along the path to releasing production versions of the “Geneva” software family, which includes the server, framework, and CardSpace. I’m personally particularly proud of all the interop work that has been done in preparation for this release. I believe that you’ll find it to be high-quality and interoperable with others’ identity software using WS-*, SAML 2.0, and Information Cards.
For more details, see What’s New in Beta 2 on the “Geneva” Team Blog. Visit the “Geneva” information page. Check out the Identity Developer Training Kit. Learn from team experts on the ID Element show. Download the beta. And let us know how it works for you, so the final versions can be even better.
Enjoy!
![]() This week the Information Card Foundation marked two significant developments at the European Identity Conference: the formation of the German-language chapter of the ICF, and receiving the European Identity Award for Best New Standard.
This week the Information Card Foundation marked two significant developments at the European Identity Conference: the formation of the German-language chapter of the ICF, and receiving the European Identity Award for Best New Standard.
The inaugural meeting of the German-language D-A-CH chapter was exciting. About 25 people attended representing at least 17 companies and organizations. A highlight was presentations by Fraunhofer FOKUS, Deutsche Telekom, CORISECIO, Siemens, Universität Potsdam, and Microsoft about their Information Card work. Lots of good things happening! Also see the ICF post about the chapter.

Receiving the European Identity Award for Best New Standard was a significant honor for the foundation, and a mark of the maturing of the Information Card ecosystem. Also see the ICF post about the award.

Sehr aufregend!
On the Kona coast of Hawaii, there’s a tradition of writing messages on the black lava flows using the white coral that washes up on the beaches. On a whim, we added a message of our own. You’ll find it about 12 miles north of the Kona Airport on the west side of the Queen Kaahumanu highway at 19°53.6759’N × 155°53.6407’W.
![]()
Close-up
![]()
My co-conspirators with their artwork
![]()
In context
![]()
And me
![]() Microsoft published a knowledge base article today giving examples of intermediate data values produced when generating actual PPID, ClientPseudonym, and Signing Key values. These examples use the algorithms specified in ISIP 1.5 to go behind the scenes of specific OSIS interop computations.
Microsoft published a knowledge base article today giving examples of intermediate data values produced when generating actual PPID, ClientPseudonym, and Signing Key values. These examples use the algorithms specified in ISIP 1.5 to go behind the scenes of specific OSIS interop computations.
In particular, the article shows how to correctly generate the PPID and Signing Key values for the test Selector_Constructs_Site-Specific_Identifiers_for_Self-Issued_Cards and how to generate the ClientPseudonym value for the test Selector_Support_for_Non-Auditing_Cards. These examples are also highly relevant to the tests Selector_PPID_Construction_for_RP_using_EV_SSL, Selector_Support_for_Auditing-Optional_Cards, and Selector_Support_for_Auditing_Cards.
Thanks to Toland Hon of the “Geneva” test team for writing this useful article.
 Sandy Porter of Avoco Secure recently let me know that their secure2trust document security product now supports both document signing and document access control using managed Information Cards. The cards and the Avoco software enable perimeterless, secured access to documents and online web form signing.
Sandy Porter of Avoco Secure recently let me know that their secure2trust document security product now supports both document signing and document access control using managed Information Cards. The cards and the Avoco software enable perimeterless, secured access to documents and online web form signing.
Avoco has hosted an instance of their Identity Provider and sample document signing and document access control scenarios online, so people can give it a try now. Using the “Create an ID” tab at https://www.secure2cardspace.com/ to create a card, and then following the instructions at the “Securing with Identity” tab, I was able to obtain a document a document that can only be opened by using the card I created.
When I open this doc (in my case, “Mike Jones.docx”), CardSpace is launched. When I submit my card, access control is granted and the document shown below is opened.
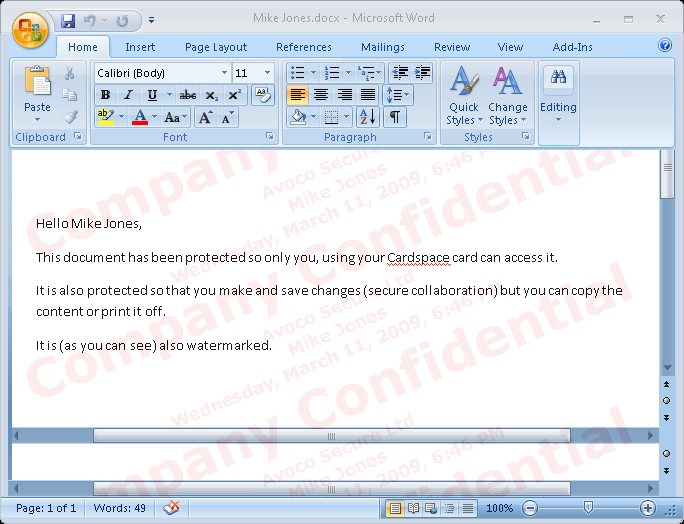
For more information, see the page “Create and Manage your own Digital Identities with Avoco Secure’s Identity Provider“, their https://www.secure2cardspace.com/ demo site, and also try document signing using your Avoco Secure managed card at http://www.secure2signonline.com/.
 At a typical conference, you listen to thought leaders; at the Internet Identity Workshop unconference, you and your peers lead together.
At a typical conference, you listen to thought leaders; at the Internet Identity Workshop unconference, you and your peers lead together.
Be a part of it: May 18-20, 2009 at the Computer History Museum, Mountain View, California. Register now!
Special bonus offer: Continuing a tradition dating back to the second IIW, Microsoft will be sponsoring a dinner for conference participants.
![]()
 Today OASIS announced the commencement of the 60-day public review period for the Identity Metasystem Interoperability Version 1.0 specification. This spec is based upon, and compatible with, the Identity Selector Interoperability Profile V1.5 (ISIP 1.5) specification and related Information Card documents submitted to the IMI TC. My sincere thanks to my fellow committee members for their diligence and promptness in reviewing and improving the specification drafts, enabling us to reach today’s milestone on a timely basis. Let the public review begin!
Today OASIS announced the commencement of the 60-day public review period for the Identity Metasystem Interoperability Version 1.0 specification. This spec is based upon, and compatible with, the Identity Selector Interoperability Profile V1.5 (ISIP 1.5) specification and related Information Card documents submitted to the IMI TC. My sincere thanks to my fellow committee members for their diligence and promptness in reviewing and improving the specification drafts, enabling us to reach today’s milestone on a timely basis. Let the public review begin!
![]()
![]() Microsoft has released an additional rendering of the Information Card Icon with a 3:2 aspect ratio, which can be used in addition to the existing 10:7 aspect ratio renderings. Quoting from the updated Frequently Asked Questions document:
Microsoft has released an additional rendering of the Information Card Icon with a 3:2 aspect ratio, which can be used in addition to the existing 10:7 aspect ratio renderings. Quoting from the updated Frequently Asked Questions document:
Q: When should the 3:2 aspect ratio version of the icon be used?
A: The 3:2 aspect ratio rendering is intended for use in visual contexts when a 3:2 aspect ratio rendering of either an Information Card image or the icon may be displayed. Having a 3:2 aspect ratio rendering of the Icon (in particular, a 120×80 pixel rendering) allows it to be the same size as an Information Card image, and thus, enables the interchangeable display of the Icon or an Information Card image.
If you have a need for a 3:2 aspect ratio rendering of the icon, you can get it now from the updated download package. You can visually compare 114×80 and 120×80 renderings of the icon in this post.
Orange, eBay, and Microsoft teamed up to demonstrate the CardSpace “Geneva” experience at TechEd in Barcelona. In the demo, an Orange-issued Information Card was used to sign into eBay with an early version of CardSpace “Geneva”. This post shows you the user experience we jointly developed. (And yes, this was running code — not a mockup.)
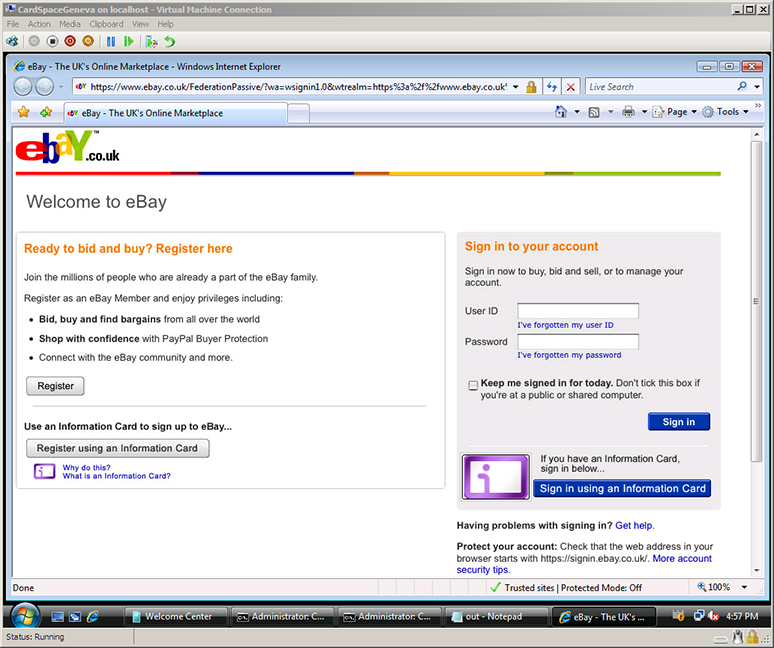
The user can sign into eBay either with a username and password or with an Information Card.
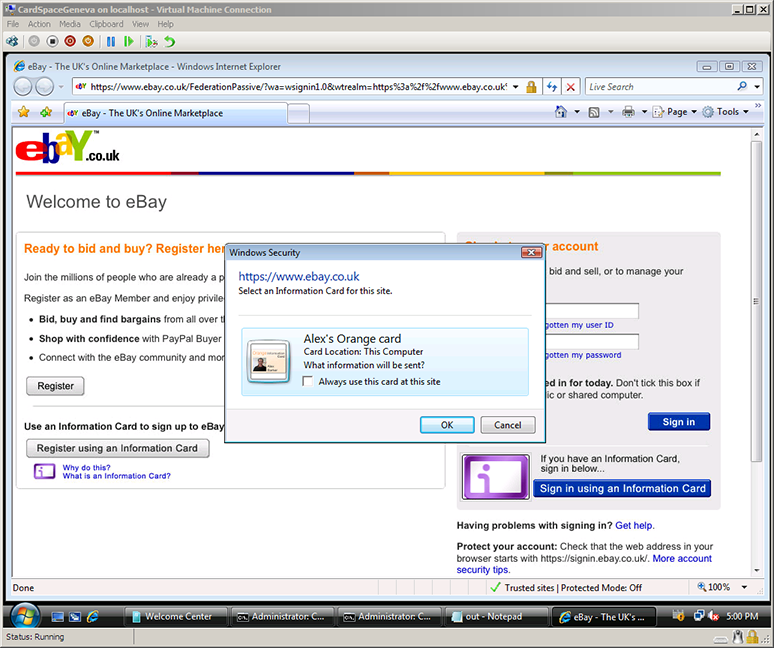
After clicking the Information Card icon in the first screen (the purple “i” symbol) to sign in with a card, CardSpace shows Alex that his Orange Information Card can be used to sign into eBay.
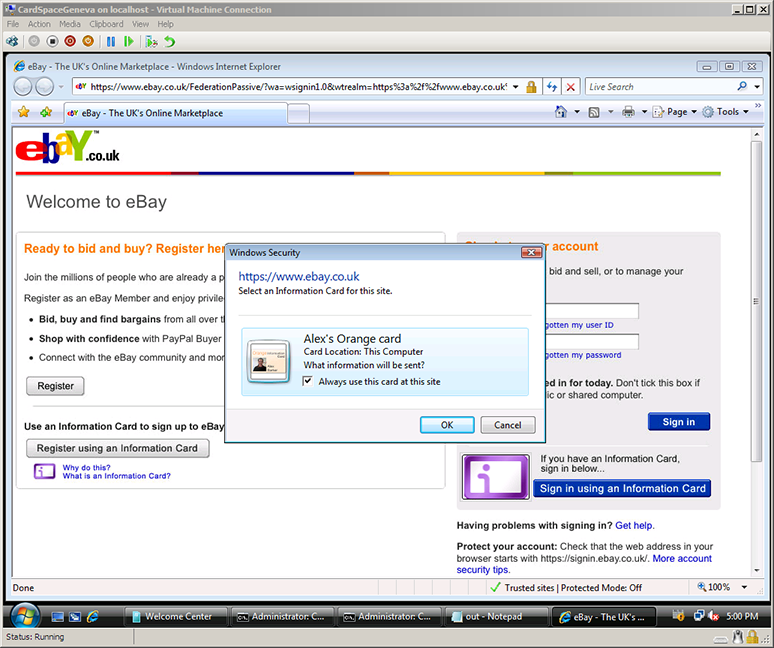
Alex decides that he always wants to sign into eBay with his Orange card, and so checks the “Always use this card at this site” box for the card.

After clicking “OK” to submit his card, Alex is logged into eBay.

eBay lets Alex see details about his login.
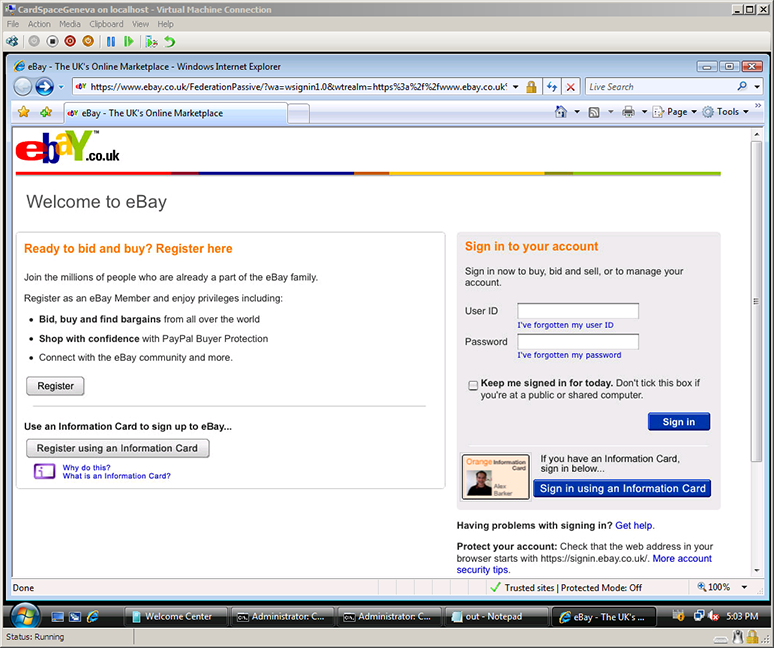
Alex has logged out, but is ready to log into eBay again. This time, rather than showing the Information Card icon, Alex’s Orange card is shown and is ready to use, courtesy of the CardSpace CardTile. Now a single click will submit his card, logging him in again.

My thanks to Dale Olds for pointing out that the SUSE Linux distribution now contains an Identity Selector — DigitalMe (from the Bandit Project). He’s right — it’s important to mark significant milestones such as these. That’s now two platforms and counting…
 As announced in Dale Olds’ post Information Card breakthrough with Novell Access Manager 3.1, Novell has released a version of Access Manager that adds support for Information Cards and WS-Federation, partially courtesy of the Bandit Team. I was on the show floor at BrainShare in March 2007 when Novell first demonstrated WS-Federation interop (showing eDirectory users on Linux accessing SharePoint on Windows via an early version of Access Manager and ADFS), so I’m particularly glad to see that the scenarios we jointly demonstrated then can now be deployed by real customers.
As announced in Dale Olds’ post Information Card breakthrough with Novell Access Manager 3.1, Novell has released a version of Access Manager that adds support for Information Cards and WS-Federation, partially courtesy of the Bandit Team. I was on the show floor at BrainShare in March 2007 when Novell first demonstrated WS-Federation interop (showing eDirectory users on Linux accessing SharePoint on Windows via an early version of Access Manager and ADFS), so I’m particularly glad to see that the scenarios we jointly demonstrated then can now be deployed by real customers.
It was also at that BrainShare where Novell demonstrated the first cross-platform Identity Selector (an event significant enough that I decided it was time to start blogging). It’s great to likewise see Novell’s Information Card work progress from show-floor demos to shipping product. Congratulations to Novell and the Bandits!
 The Internet Safety Technical Task Force has released its report on online child safety: Enhancing Child Safety and Online Technologies: Final Report of the Internet Safety Technical Task Force to the Multi-State Working Group on Social Networking of State Attorneys General of the United States. During its year-long effort, the task force surveyed existing research and evaluated technologies that are relevant to child safety online.
The Internet Safety Technical Task Force has released its report on online child safety: Enhancing Child Safety and Online Technologies: Final Report of the Internet Safety Technical Task Force to the Multi-State Working Group on Social Networking of State Attorneys General of the United States. During its year-long effort, the task force surveyed existing research and evaluated technologies that are relevant to child safety online.
One thing noticeably absent from the report, given the number of different technologies presented to and discussed by the task force, is references to any of them. In the end, the task force took the position that while technologies can help, that none is a silver bullet, and none are a substitute for parents and other adults who are active in children’s lives. I have to agree with them.
The Technical Advisory Board appointed by the task force evaluated possible technological approaches to making children safer online. A number of its members were individuals active in the identity and security communities, including Ben Adida of Harvard, Todd Inskeep of Bank of America, RL “Bob” Morgan of the University of Washington, and Danny Weitzner of MIT. The Technology Advisory Board Report summary included:
In sum, the TAB review of the submitted technologies leaves us in a state of cautious optimism, with many submissions showing promise. The children’s online safety industry is evolving, and many of the technologies we reviewed were point solutions rather than broad attempts to address the children’s safety online as a whole. There is, however, a great deal of innovation in this arena as well as passionate commitment to finding workable, reasonable solutions from companies both large and small. Thus, the TAB emerged from its review process encouraged by the creativity and productivity apparent in this field.
By the end of the review process, the TAB ultimately determined that no single technology reviewed could solve every aspect of online safety for minors, or even one aspect of it one hundred percent of the time. But clearly there is a role for technology in addressing this issue both now and in the future, and most likely, various technologies could be leveraged together to address the challenges in this arena.
Some critics may object to the use of technology as a solution, given the risk of failure and lack of total certainty around performance. However, the TAB believes that although it is indeed true that even the cleverest, most robust technology can be circumvented, this does not necessarily mean that technology should not be deployed at all. It simply means that – even with deployment of the best tools and technologies available to jumpstart the process of enhancing safety for minors online – there is no substitute for a parent, caregiver, or other responsible adult actively guiding and supporting a child in safe Internet usage. Likewise, education is an essential part of the puzzle. Even the best technology or technologies should be only part of a broader solution to keeping minors safer online.
Makes sense to me…
From a personal perspective, I’d like to thank the task force for giving me the opportunity to describe how Information Cards can be used to convey verified claims about individuals, and to thank IDology and Novell for making this real with a working demo of verified age cards for the task force.
I also enjoyed working with Jules Cohen and Chuck Cosson of Microsoft’s Trustworthy Computing and Law and Corporate Affairs groups on the identity technology aspects of Microsoft’s inputs to the task force. I have enormous respect for the balanced and thoughtful perspectives they brought to the discussion, as exemplified by their paper Digital Playgrounds: Creating Safer Online Environments for Children, which was submitted to the task force. Their proposal that existing offline identity proofing ceremonies could be leveraged to enhance safety online resonated with many of the task force members.
I expect media and blog coverage of the report to be active over the next few days. An early sampling includes:
- New York Times: Report Calls Online Threats to Children Overblown
- Wall Street Journal: No Easy Answer for Protecting Kids Online
- CNet: Net threat to minors less than feared
These are important and interesting issues. It’s a discussion well worth following and participating in.
 As I just announced on openid.net, OpenID Provider Authentication Policy Extension 1.0 (PAPE) has just been just been approved as an OpenID specification. Deployment of PAPE will go a long way towards mitigating the phishing vulnerabilities of password-based OpenIDs by enabling OpenID Relying Parties to request that OpenID Providers employ phishing-resistant authentication methods when authenticating users and for OpenID Providers to inform Relying Parties whether this (and other) authentication policies were satisfied.
As I just announced on openid.net, OpenID Provider Authentication Policy Extension 1.0 (PAPE) has just been just been approved as an OpenID specification. Deployment of PAPE will go a long way towards mitigating the phishing vulnerabilities of password-based OpenIDs by enabling OpenID Relying Parties to request that OpenID Providers employ phishing-resistant authentication methods when authenticating users and for OpenID Providers to inform Relying Parties whether this (and other) authentication policies were satisfied.
It’s tempting to say that the approval of the specification is the fulfillment of the promise of the OpenID/CardSpace collaboration for phishing-resistant authentication introduced by Bill Gates and Craig Mundie the RSA Security Conference last year, but it’s really just an enabling step. The true value of PAPE will come when it is widely deployed by security-conscious OpenID Relying Parties, and the use of phishing-resistant authentication methods, such as Information Cards and others, is widespread and commonplace. Let the deployments begin!
At the 25th Chaos Communication Congress (CCC) today, researchers will reveal how they utilized a collision attack against the MD5 algorithm to create a rogue certificate authority.
As Scott says, this is pretty big news, so I encourage you to read his post and the paper describing the breach. He also writes that “affected CAs are switching to SHA-1”.
This episode immediately reminded me of a principle that Kim often espouses:
The way to design securely is to assume your system WILL be breached and create a design that mitigates potential damage.
I’ll leave it to others to debate whether CAs switching to SHA-1 is likely to be an effective mitigation in the long term and to discuss how long it will take before this particular breach has been worked around. But this sure provides (more) convincing evidence that designing systems with the assumption that they will be breached is essential to those systems’ robustness and long-term viability.
 The OpenID Foundation just completed its first election for community board seats. 17 candidates ran for 7 seats and 175 out of 217 eligible members voted in the election. My congratulations to Snorri Giorgetti, Nat Sakimura, Chris Messina, David Recordon, Eric Sachs, Scott Kveton, and Brian Kissel for their election as community board members. I look forward to serving on the board with them in January, along with my fellow corporate board members DeWitt Clinton, Tony Nadalin, Gary Krall, and Raj Mata. It looks like a great board!
The OpenID Foundation just completed its first election for community board seats. 17 candidates ran for 7 seats and 175 out of 217 eligible members voted in the election. My congratulations to Snorri Giorgetti, Nat Sakimura, Chris Messina, David Recordon, Eric Sachs, Scott Kveton, and Brian Kissel for their election as community board members. I look forward to serving on the board with them in January, along with my fellow corporate board members DeWitt Clinton, Tony Nadalin, Gary Krall, and Raj Mata. It looks like a great board!
 Dick Hardt, independent thinker, entrepreneur, Identity 2.0 leader, fellow OpenID board member, and friend, is Coming to America and joining Microsoft. Dick, I’m looking forward to working with you as a colleague and expect your perspectives to change what we do and make us better for it.
Dick Hardt, independent thinker, entrepreneur, Identity 2.0 leader, fellow OpenID board member, and friend, is Coming to America and joining Microsoft. Dick, I’m looking forward to working with you as a colleague and expect your perspectives to change what we do and make us better for it.
P.S. Lest any of you think I’m being rude, the title of this post is a tribute to Dick’s famous (infamous?) talk title “Who is the Dick on your site?“. :-)
 The directions we’ve taken CardSpace “Geneva” are strongly shaped by feedback we received about the first version of CardSpace. One of the most frequently heard feedback points was to make the user experience less disruptive. For instance, Ashish Jain wrote about “Too many clicks”.
The directions we’ve taken CardSpace “Geneva” are strongly shaped by feedback we received about the first version of CardSpace. One of the most frequently heard feedback points was to make the user experience less disruptive. For instance, Ashish Jain wrote about “Too many clicks”.
The new “CardTile” feature, where the image of the last card used at a site can be displayed on the site’s page, enables two-click card submission, while still providing the user feedback about the card that will be used by default. The screen shot below shows an example of the CardTile in use, displaying the image of the most recently used card in the page.
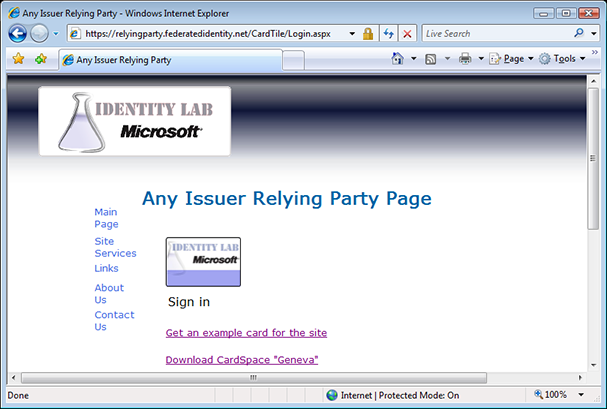
The “Always use this card at this site” feature takes this a step further, enabling true one-click submission to sites where you have already used a card. See the recent CardSpace “Geneva” Selection Experience post for more details.
But back now to the subject of this post… The FederatedIdentity.net team has created a relying party page using the CardTile at https://relyingparty.federatedidentity.net/AnyIssuerRelyingParty/Login.aspx?tile=true. It should work both with selectors that do and don’t support the CardTile feature. Try it yourself!
