Fun Communications‘ site idtheft.fun.de lets you mount your very own man-in-the-middle based phishing attack against the OpenID provider of your choosing. Rather than redirecting you to the OpenID provider you specify, it instead redirects you to a page impersonating the OpenID provider, created using content scraped from the real site behind the scenes.
This is the same kind of attack shown in Kim’s phishing video. idtheft.fun.de lets you have the fun of doing it yourself!
I tried it myself with several OpenID providers I use. Predictably, I was typically able to “steal” the passwords for OpenIDs when logging into them with passwords and hijack the resulting logged-in sessions. “Protecting” an account with a one-time-password (OTP) device did nothing to stop this; my “attack” still succeeded in hijacking the session established using a password in combination with an OTP value.
Two things did defeat these attacks. Because Information Cards generate site-specific sign-in information and the attacker’s site is different than the authentic site, even when I was “tricked” into submitting an Information Card to the imposter site, it didn’t give the imposter the ability to log into the real site. No shared secret was present to steal and no session was established to hijack.
The other thing that defeated this specific attack was the use of JavaScript in the sign-in process by the OpenID provider. While a slightly more sophisticated attack could almost certainly get past this obstacle, idtheft.fun.de apparently doesn’t correctly mimic JavaScript site features like “Sign In” buttons invoking an onclick method.
This ability to both phish passwords and hijack the resulting logged-in sessions is exactly why I and others are working on finishing the OpenID Provider Authentication Policy Extension (PAPE) extension. As I wrote when the first draft was published, PAPE enables “OpenID relying parties to request that a phishing-resistant authentication method be used by the OpenID provider and for providers to inform relying parties whether a phishing-resistant authentication method, such as Windows CardSpace, was used.” It’s time for PAPE to become an OpenID standard.
What follows are screen shots from a successful phishing attack and a thwarted one — both against the same OP. The difference is whether passwords or Information Cards were used to log in.
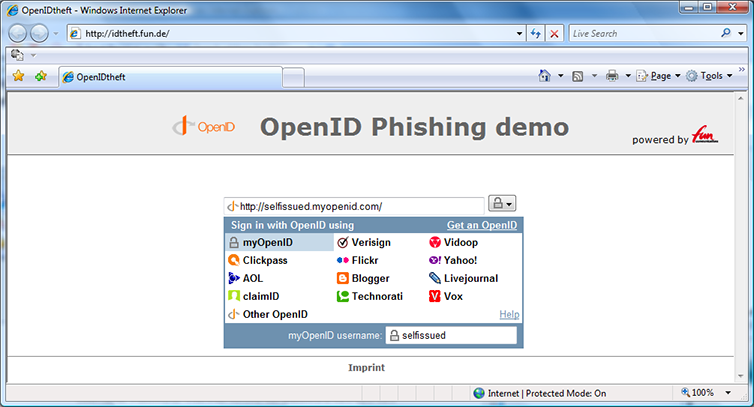
Figure 1: About to mount my attack against my OpenID at myopenid.com. I’ve typed the URL of my OpenID into the relying party.
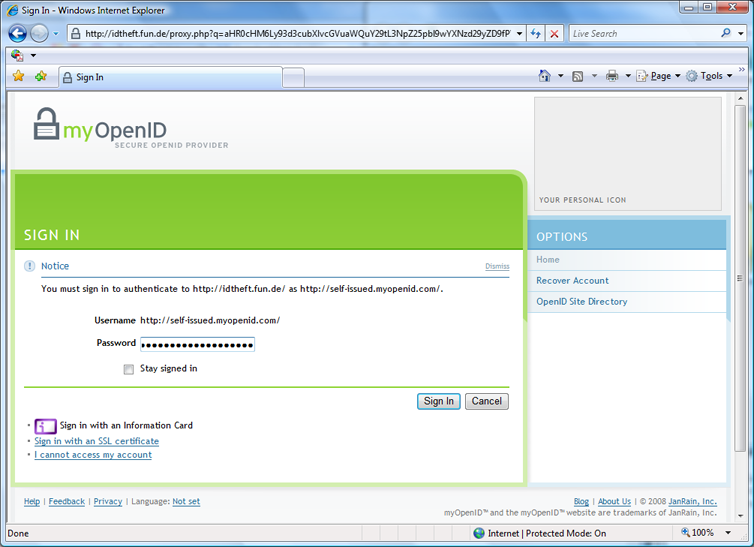
Figure 2: Next, I’m logging in with a password. An observant user could notice several things wrong: the address bar shows the imposter’s URL, the imposter’s URL is present in the “You must sign in to authenticate to …” message, and the “Your Personal Icon” space is blank. Unfortunately, there is strong evidence that users are not observant.
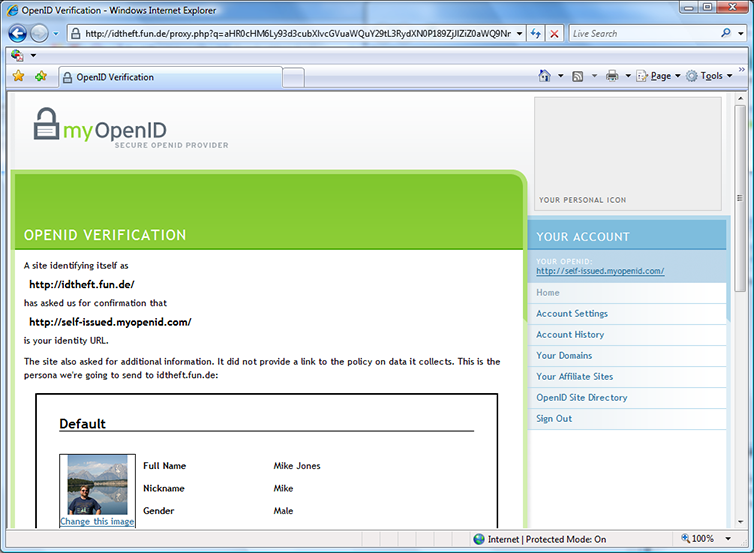
Figure 3: Phishing already accomplished. Same cues are present that something’s amiss. Of course, a more sophisticated attack could replace the imposter’s URL in the page with the “real one” in both of these screens, eliminating the most obvious cue. I scroll down and click “Allow Once”.
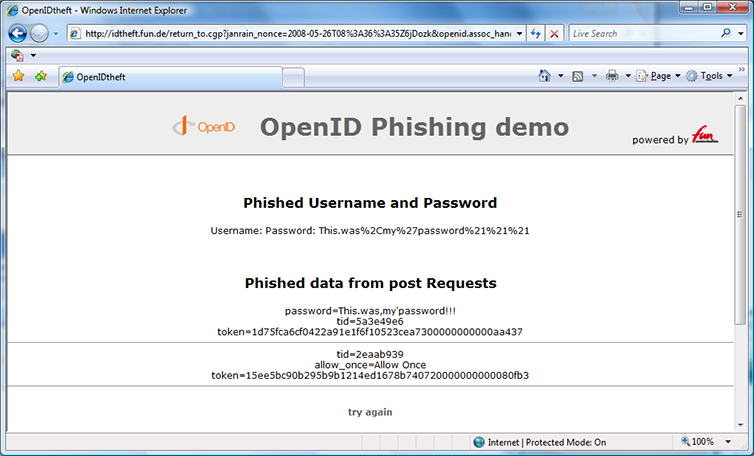
Figure 4: Result after being redirected back to the “relying party”. Yes, that was my real password.
Next, I tried to attack my account again but was surprised that I wasn’t asked to log in this time. Of course — the attacker’s session was already logged in! So I signed out as the man-in-the-middle (that was weird), enabling me to try again.
My next steps looked just like Figures 1 and 2, except instead of typing a password I clicked the purple Information Card button. This brought me to:
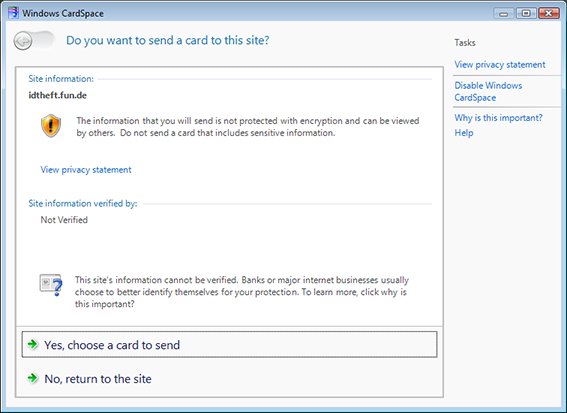
Figure 5: CardSpace informs me that I’ve never sent a card to this site before. An observant user would realize that they don’t normally see this screen and might decline. But then, we’ve already discussed how observant users aren’t. I click “Yes”, choose the card I normally use to log into myopenid.com, and send it.
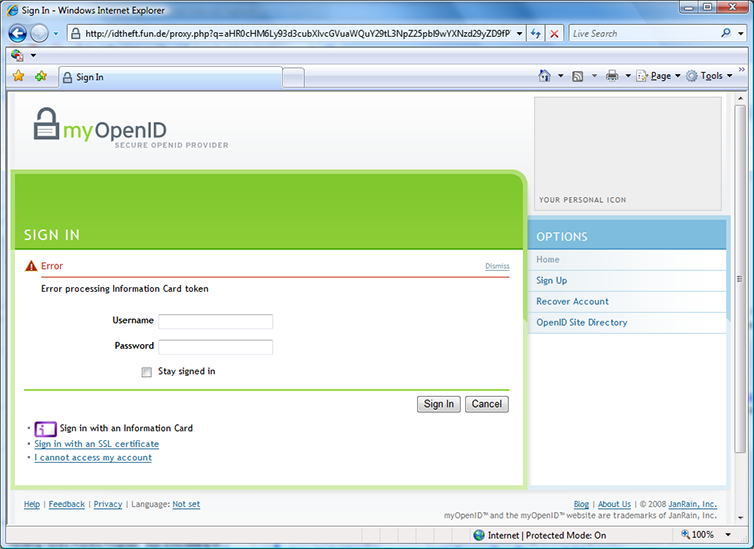
Figure 6: Phishing prevented. “Error processing Information Card token” isn’t the most informative error message I’ve ever seen but behind it is great news: the phishing attack failed because the token constructed for the imposter site wasn’t usable at the real site.
And thanks to idtheft.fun.de, you can try this at home!

Carsten Pötter
Carsten Pötter
Michael Graves
Michael Graves
Mike Jones
Mike Jones
Kevin Fox
Kevin Fox
Mike Jones
Mike Jones
http://simonwillison.net/
http://simonwillison.net/
Axel Nennker
Axel Nennker
Johannes Feulner
Johannes Feulner